Difference between revisions of "User:Darwin2049/ChatGPT4/Theoretical"
Darwin2049 (talk | contribs) |
Darwin2049 (talk | contribs) |
||
| (6 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
[[File:OPENAI.png|left|220px]] | [[File:OPENAI.png|left|220px]] | ||
'''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://arguably.io/index.php?title=ChatGPT4-Questions/User:Darwin2049/Overview&action=edit Overview]</SPAN>'''''<BR /><BR /> | '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://arguably.io/index.php?title=ChatGPT4-Questions/User:Darwin2049/Overview&action=edit Overview]</SPAN>'''''<BR /><BR /> | ||
'''''<Span Style="COLOR: | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Theoretical and Speculative Risks.</SPAN>''''' A review of reports that have emerge in the weeks following the release of Chat GPT4 will show that the number and coverage has proliferated considerably. Attempting to summarize the full impact of this new technology is proving to be a moving target and therefore increasingly difficult to summarize. Several actual or hypothetical examples follow that might serve as starting points for further discussion and analysis. As of June 2023 there has been an explosion of discussions, presentations, documentaries and news reports. These have surfaced in the broader main stream media as well as in the more specialized reporting channels. The result is that those initial topical starting points (listed below) will doubtless be out of date. Therefore the topic obliges revisiting periodically in the upcoming weeks and months. | ||
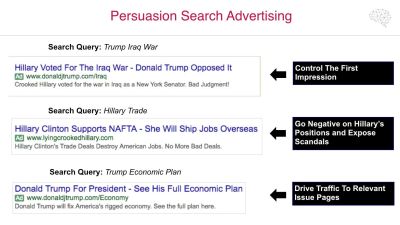
*'''''<Span Style="COLOR: | *'''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Influence and Persuasion.</SPAN>''''' Viewers of Netflix can find on that site a documentary titled '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.google.com/search?q=the+great+hack&tbm=vid&source=lnt&tbs=dur:m&sa=X&ved=2ahUKEwjA0OTO5v__AhXmLUQIHfnwAlIQpwV6BAgMEAg&biw=1509&bih=786&dpr=2.25 The Great Hack]''''' (Youtube video links). This documentary details how the company named '''''FaceBook''''' bought a British company named '''''Cambridge Analytica'''''. The documentary details how Cambridge Analytica used access to the massive FaceBook system to categorize eligible voters in both the US and the UK in terms of their political, social and economic values. | ||
Using these insights were able to craft highly specific "hot button" messages to specific voters with the intent to influence voting behavior. These messages were structured such that their true purpose remained obscured. | Using these insights were able to craft highly specific "hot button" messages to specific voters with the intent to influence voting behavior. These messages were structured such that their true purpose remained obscured. | ||
| Line 9: | Line 9: | ||
[[File:CambAnalytic00.jpeg|left|400px|Cambridge Analytica Influencing Strategy]] | [[File:CambAnalytic00.jpeg|left|400px|Cambridge Analytica Influencing Strategy]] | ||
* '''''<Span Style="COLOR: | * '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Narratives: </SPAN>'''''Highly realistic, plausible narratives and counter-narratives are now effortlessly possible; these might include: | ||
'''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.vice.com/en/article/epvxn7/ai-political-ads-republicans-biden Rumors, Disinformation]:</SPAN>''''' we should expect that these narratives will exhibit remarkable saliency and credibility; but in many cases will prove to be groundless; leading the elaboration of this area will probably be the development of divisive social/political narrative creation; i.e. fake news; | '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.vice.com/en/article/epvxn7/ai-political-ads-republicans-biden Rumors, Disinformation]:</SPAN>''''' we should expect that these narratives will exhibit remarkable saliency and credibility; but in many cases will prove to be groundless; leading the elaboration of this area will probably be the development of divisive social/political narrative creation; i.e. fake news; | ||
| Line 18: | Line 18: | ||
A careful observer will note that the company adheres to a cautious stylistic approach that is calculated to be "middle of the road" or "mainstream". Insofar as it uses sketches of past or present individual the presentation rarely if ever presents them using a caricature approach. We should probably not expect the new wave of animated providers to be so constrained. | A careful observer will note that the company adheres to a cautious stylistic approach that is calculated to be "middle of the road" or "mainstream". Insofar as it uses sketches of past or present individual the presentation rarely if ever presents them using a caricature approach. We should probably not expect the new wave of animated providers to be so constrained. | ||
[[File:rsa00.jpg|right| | [[File:rsa00.jpg|right|650px|RSA Animate Messaging]] | ||
Looking forward we should expect to see any number of new companies springing forth that use this same approach but will instead add not only contemporaneous color sketches to support the spoken narrative but rather we should expect to see much more [https://www.youtube.com/watch?v=nJmGrNdJ5Gw&ab_channel=RSA detailed animations] of these sketches. Further, we should also expect that they will cover topics across a spectrum of beliefs and opinions. | Looking forward we should expect to see any number of new companies springing forth that use this same approach but will instead add not only contemporaneous color sketches to support the spoken narrative but rather we should expect to see much more [https://www.youtube.com/watch?v=nJmGrNdJ5Gw&ab_channel=RSA detailed animations] of these sketches. Further, we should also expect that they will cover topics across a spectrum of beliefs and opinions. | ||
| Line 24: | Line 24: | ||
Especially common will be presentations on a range of social and cultural topics. Because these will be available on platforms other than the now popular youtube.com we can expect that there will be considerably greater latitude in the topical content and its adherence to "community standards", i.e. considerably relaxed oversight and censorship. | Especially common will be presentations on a range of social and cultural topics. Because these will be available on platforms other than the now popular youtube.com we can expect that there will be considerably greater latitude in the topical content and its adherence to "community standards", i.e. considerably relaxed oversight and censorship. | ||
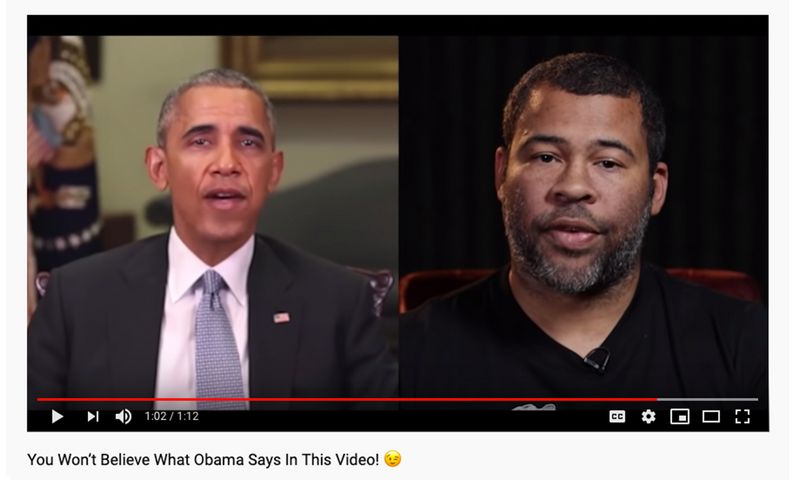
*'''''<Span Style="COLOR: | *'''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Manipulation - Persuasive Messaging. </SPAN>''''' Commercial deep fake video tools enable a skilled user to create videos that are seamless and utterly convincing. These tools allow a user to create a scripted or unscripted video. Amateur actors or non-professional stand-ins can be used to recite a prewritten script. Or a speaker can carry on extemporaneously. After a recording of the speaker is captured the facial image of another individual can be smoothly mapped onto the face of the actor. '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.youtube.com/watch?v=S951cdansBI&ab_channel=JohnnyHarris The result is stunning]. </SPAN>''''' Even a trained and attentive observer will find it difficult to impossible to determine that a switch has been performed. This capability means that '''''<SPAN STYLE="COLOR:BLUE">any kind of messaging can be created for any purpose </SPAN>'''''. A small team can create a message that possesses powerful messaging and inflammatory content that can motivate people to take individual or collective action outside of usual social bounds. | ||
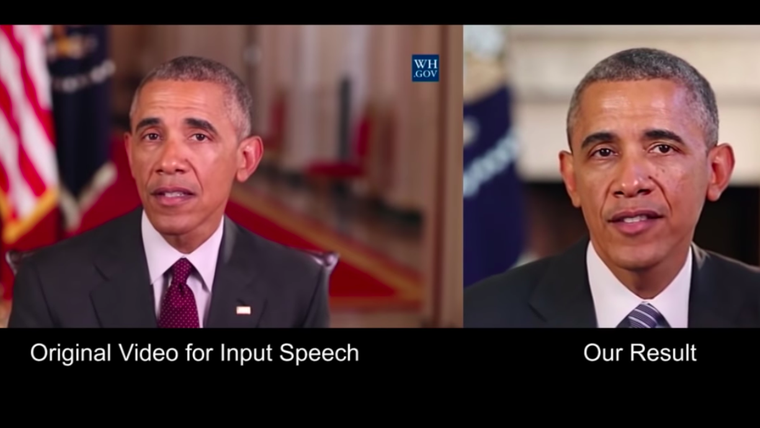
*'''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://rollcall.com/2023/05/25/ai-could-sway-the-2024-elections-campaign-pros-say-but-not-like-you-think/ Political Messaging]:</SPAN>''''' individuals seeking political office create and disseminate their campaign platform statements and disseminate them throughout their respective electoral districts; creating these to address local hot button issues can now be done very quickly. In the political context the facial image of a well known person, a celebrity or politician can be used to appear to be promoting a particular stance. In the following we can see the use of deep face video technology using a known image of former President Obama to promote a position. Note that the face of any other individual can be used. The target face is the one that will be available for viewing. | *'''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://rollcall.com/2023/05/25/ai-could-sway-the-2024-elections-campaign-pros-say-but-not-like-you-think/ Political Messaging]:</SPAN>''''' individuals seeking political office create and disseminate their campaign platform statements and disseminate them throughout their respective electoral districts; creating these to address local hot button issues can now be done very quickly. In the political context the facial image of a well known person, a celebrity or politician can be used to appear to be promoting a particular stance. In the following we can see the use of deep face video technology using a known image of former President Obama to promote a position. Note that the face of any other individual can be used. The target face is the one that will be available for viewing. | ||
[[File:deepfake00.png|250|left|Fake Obama Message]] | [[File:deepfake00.png|250|left|Fake Obama Message]] | ||
'''''<Span Style="COLOR: | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Detecting clever deceptions will be extraordinarily difficult</SPAN>''''' to detect and falsify. '''''<Span Style="COLOR:BLUE;BACKGROUND:YELLOW">[https://www.youtube.com/watch?v=S951cdansBI&ab_channel=JohnnyHarris Deep Fake Video]</SPAN>''''' can as well be used to deliver a statement or speech that they never have in the actual real world. For instance we can see how an existing image of former President Obama can be used to create a new image of President Obama saying things that he has never said. The possibility of determining if Obama actually made the statements that can be attributed to him becomes very very difficult. | ||
Or as mentioned above, a small team can use a commercial tools such as XYZ and totally private individuals to create a deep fake video and ascribe a statement to a celebrity or politician. Again, determining if the video was real will become remarkably difficult. | Or as mentioned above, a small team can use a commercial tools such as XYZ and totally private individuals to create a deep fake video and ascribe a statement to a celebrity or politician. Again, determining if the video was real will become remarkably difficult. | ||
| Line 41: | Line 41: | ||
In a similar case '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.youtube.com/watch?v=NBJvljFBuvg&ab_channel=AZFamily%7CArizonaNews a scammer demanded ransom money]</SPAN>''''' using the deception that her daughter had been kidnapped. | In a similar case '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.youtube.com/watch?v=NBJvljFBuvg&ab_channel=AZFamily%7CArizonaNews a scammer demanded ransom money]</SPAN>''''' using the deception that her daughter had been kidnapped. | ||
* | * '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Entertainment </SPAN>''''' | ||
Those who follow Dr Alan Thompson will know that he uses an avatar that he has labeled Leta. The Leta avatar is a synthetic person with remarkably lifelike features and behavior. Over the course of a "conversation" with Leta, Dr Thompson engages in discussing a range of topics of the day. He has clarified that in order to make the appearance of a dialog seem realistic and authentic he spells out that he has to resort to a number of behind the scene actions. These actions result in what looks like an ongoing real time dialog. | Those who follow Dr Alan Thompson will know that he uses an avatar that he has labeled Leta. The Leta avatar is a synthetic person with remarkably lifelike features and behavior. Over the course of a "conversation" with Leta, Dr Thompson engages in discussing a range of topics of the day. He has clarified that in order to make the appearance of a dialog seem realistic and authentic he spells out that he has to resort to a number of behind the scene actions. These actions result in what looks like an ongoing real time dialog. | ||
| Line 52: | Line 52: | ||
Accordingly it is not far fetched to imagine a situation wherein a video were to be created of a recent prominent public figure having a conversation with another figure. The other conversationalist might be portrayed as being a member of an illegal organization; this could be played out such that the prominent individual appears to be engaging in weapons trafficking's. | Accordingly it is not far fetched to imagine a situation wherein a video were to be created of a recent prominent public figure having a conversation with another figure. The other conversationalist might be portrayed as being a member of an illegal organization; this could be played out such that the prominent individual appears to be engaging in weapons trafficking's. | ||
*'''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://ts2.space/en/chat-gpt-4-in-the-film-industry-scriptwriting-editing-and-more/ Scriptwriting]</SPAN>''''' (see also:) | *'''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://ts2.space/en/chat-gpt-4-in-the-film-industry-scriptwriting-editing-and-more/ Scriptwriting]</SPAN>''''' (see also:) '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://nerdynovelist.com/write-a-novel-with-chatgpt/ Novels]:</SPAN>''''' a remarkable capability that CG4 has shown itself capable of is in the creation of narrative that can be used for the creation of a screen play or novel; it is capable of generating; it is capable of generating seemingly realistic characters from just a few initial prompts; these prompts can be further elaborated upon and refined to the point that a very believable character can be generated; a set of characters can be created each of which has their own motives, concerns, flaws and resources; using a set of these fictitious characters it is entirely possible to create a story line in which they each interact with each other; hence a whole screen play or even possibly a novel can be developed in record time; | ||
*'''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.youtube.com/watch?v=aIDSmgsT4p8&ab_channel=SECourses NPC]:</SPAN>''''' immersive role play: along similar lines CG4 is capable of being used to create artificial environments that are suitable for online immersive role playing games; these environments can possess any features or characteristics imaginable; if one were to look a short bit forward in time the industry of interactive role playing games may well experience an explosion of new possibilities; | *'''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.youtube.com/watch?v=aIDSmgsT4p8&ab_channel=SECourses NPC]:</SPAN>''''' immersive role play: along similar lines CG4 is capable of being used to create artificial environments that are suitable for online immersive role playing games; these environments can possess any features or characteristics imaginable; if one were to look a short bit forward in time the industry of interactive role playing games may well experience an explosion of new possibilities; | ||
* | *'''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.howtogeek.com/881659/how-to-create-chatgpt-personas-for-every-occasion/ Synthetic Personalities]:</SPAN>''''' given the resources in terms of time and insight a knowledgeable user can use CG4 to create a fictitious personality; this personality can be imbued with traits, habits of thought, turns of phrase, an autobiographical sketch of arbitrary depth and detail; it can then be invoked as an interaction medium to engage with a user; these can mean engaging with an artificial personality with broad insights about the world or much more narrow but deep insights into specific knowledge domains; interacting with such a fictitious or synthetic personality might bear a powerful resemblance to training a surprisingly sophisticated dog; except that in this case the “dog” would be capable of sustaining very high levels of dialog and interaction. | ||
*'''''<Span Style="COLOR: | *'''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Scalable Composite CPs. </SPAN>'''''When we examine the emerging directions that tool creation are going in then we should expect to see tools emerge that enable the creation of far larger ensembles of CP4, or its derivatives. These scaled up versions might be available as "off the shelf" modules that offer "plug and play" capability. This kind of interconnectivity and interoperability will mean that highly refined and very unique combinations of capabilities will emerge that will be dedicated to perform specific tasks at levels of sophistication not known today. Ilya Sutskiver has intimated that it might be possible to have an ensemble of "friends" who are the "smartest people you know" who are all working at electronic speed. They each would possess expert levels of competence and knowledge about specific domain areas that are germane to a user's goals. Current efforts with mega-personas suggest that this time has arrived. We may well be witnessing the emergence of what Marvin Minsky hypothesized in his Society of Mind book. </SPAN>''''' | ||
*'''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.youtube.com/watch?v=azwt2pxn3UI&ab_channel=Frontiers Advisors (Harari – 15:25)].</SPAN>''''': | *'''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.youtube.com/watch?v=azwt2pxn3UI&ab_channel=Frontiers Advisors (Harari – 15:25)].</SPAN>''''': | ||
*'''''<Span Style="COLOR: | *'''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Personal Relationships (Harari – 11:30).</SPAN>''''' Interpersonal skills are often daunting for many people; socialization, economic, political, religious and other predispositions can condition the development of a gradually improving relationship, or conversely a worsening of it; being able to recognize, articulate and manage differences can be costly and time consuming; at worse they can result in costly and acrimonious separations; being able to head these pathways off before they pass a point of no return will be a huge step forward in facilitating the creation of positive relationships; | ||
*'''''<Span Style="COLOR: | *'''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Financial.</SPAN>''''' Access to quality financial advisors can be very expensive; the ability to query a system with a high level of financial expertise will propagate improved financial decisions far beyond where they currently stand, i.e. affordable only by financially well to do individuals; | ||
*'''''<Span Style="COLOR: | *'''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Political.</SPAN>''''' This might mean recognizing a local issue, creating a local community ground swell of interest then forming a political action committee to bring to a local political authority for address and resolution; | ||
*'''''<Span Style="COLOR: | *'''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Psychological.</SPAN>''''' Existing psychological systems have already demonstrated their usefulness in cases of PTSD; going forward we can envision having a personal therapist that possesses a deep understanding of an individual person’s psychological makeup; such an advisor would be capable of helping the individual to work through issues that might be detrimental to their further pursuits or advancement; | ||
* | *'''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Support, anywhere, any time.</SPAN>''''' Would we even know if the person talking on their fone using a headset is talking to an actual person on the other end? With current text to speech and speech to text we might not. Recent trials have shown that using an artificial intelligence system as a psychotherapist have shown unexpected and guardedly positive results. What happens as they become more conversant, empathetic and insightful? It might become very common to have direct access to a personal support capability at any time, wirelessly. In 2014 the '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">USC Institute for Creative Technologies trialed [https://www.youtube.com/watch?v=ejczMs6b1Q4&ab_channel=USCICT a tool SimSensei].</SPAN>''''' The intention was to use this tool as a proxy for interacting with individuals with PTSD. This approach used facial and gesture recognition to typify and categorize internal mental states of a patient. More recently CG4 has become an increasingly hot topic in the field of mental health. | ||
*'''''< | *'''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Professional Development.</SPAN>''''' Work place realities reflect the fact that social, economic and political shifts can cause surprising and sometimes dramatic changes; these might entail off shoring, downsizing, outsourcing; therefore any individual aspiring to remain on top of their professional game will need to be alert to these shifts and able to make adjustments in changing their mix of professional skills; | ||
*'''''< | *'''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Collaborative Advice.</SPAN>''''' Recent research has shown that CG4 can be configured such that it can exhibit the behavior of multiple different personalities. Recent efforts have termed this capability as '''''mega-personas. ''''' The metaphor of a team of experts might be a suitable example of how an ensemble of CG4 instances can be structured and made available. Each persona can posses specific and highly refined expertise in various domains or various aspects of a particular domain. Communicating with this kind of system would be comparable to being able to have conversations with a range of different experts. They might be configured to communicate and interact with each other or they might be configured such that they only communicated with the end user. The recent paper called '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://arxiv.org/abs/2209.06899 Out of One, Many: Using Language Models to Simulate Human Samples] '''''<SPAN STYLE="COLOR:RED"> | ||
[[FILE:Zoom01.jpg| | [[FILE:Zoom01.jpg|right|450px|Early Zoom Conference Call]] | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Collaborative Problem Solving.</SPAN>''''' (Zoom online meeting, July 2023), Most net-literate individuals will instantly grasp a reference to a communication tool such as Skype or Zoom. These have become so commonplace that we regularly see broadcast news interviews where a participant will be discussion a topic using either Zoom or Skype. | ||
With the more recent versions of Skype it is now possible to hold conferences with several dozen individuals simultaneously. With the Zoom variant one is obliged to operate as if they were hosting a meeting, conference or class event. In either case it is possible for multiple participants to interact simultaneously both verbally and visually. Which on reflection means that the existing practice of gathering a number of individuals together, typically in a meeting place, venue or room has been carried over and is being used as a proxy to repeat the process though in a geographically distributed way. | With the more recent versions of Skype it is now possible to hold conferences with several dozen individuals simultaneously. With the Zoom variant one is obliged to operate as if they were hosting a meeting, conference or class event. In either case it is possible for multiple participants to interact simultaneously both verbally and visually. Which on reflection means that the existing practice of gathering a number of individuals together, typically in a meeting place, venue or room has been carried over and is being used as a proxy to repeat the process though in a geographically distributed way. | ||
| Line 88: | Line 88: | ||
[[FILE:ColossusGuardian00.jpg|left|450px|Colossus (US) communicating instantly with Guardian (USSR)]] | [[FILE:ColossusGuardian00.jpg|left|450px|Colossus (US) communicating instantly with Guardian (USSR)]] | ||
'''''Representation Abstraction. ''''' By this we mean that there seems to be no obvious reason that we should expect to see machines communicating with each other in human language. No more so than that we expect to see a real time stock market equity price from a source such as Finance.Yahoo.com to communicate with our pc using human language. Instead they are exchanging numeric and formatting information at electronic speed. | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Representation Abstraction. ''''' By this we mean that there seems to be no obvious reason that we should expect to see machines communicating with each other in human language. No more so than that we expect to see a real time stock market equity price from a source such as Finance.Yahoo.com to communicate with our pc using human language. Instead they are exchanging numeric and formatting information at electronic speed. | ||
The 1970’s movie ‘Colossus – The Forbin Project’ was based upon a novel written by DF Jones in 1966. In the story narrative upon being switched on Colossus almost immediately detected the presence of another entity comparable to itself and expressed the desire to have a communications channel to it established. Because that other entity had been created by the Soviet Union the leadership of the US tried to prevent this from happening. Ultimately they acceded to the request and allowed for a channel to be opened. | The 1970’s movie ‘Colossus – The Forbin Project’ was based upon a novel written by DF Jones in 1966. In the story narrative upon being switched on Colossus almost immediately detected the presence of another entity comparable to itself and expressed the desire to have a communications channel to it established. Because that other entity had been created by the Soviet Union the leadership of the US tried to prevent this from happening. Ultimately they acceded to the request and allowed for a channel to be opened. | ||
'''''Bandwidth.''''' In a very short period of time Colossus and Guardian had established a means of communicating with each other symbolically. Their exchanges quickly migrated to mathematical representations. Within hours their exchanges were using representations that no human had any insight or grasp of. We should expect that the exchanges between these knowledge based systems to be comparable both in volume and complexity. In short, human intervention would simply bog down the exchange of very deep and broad knowledge elements. | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Bandwidth.''''' In a very short period of time Colossus and Guardian had established a means of communicating with each other symbolically. Their exchanges quickly migrated to mathematical representations. Within hours their exchanges were using representations that no human had any insight or grasp of. We should expect that the exchanges between these knowledge based systems to be comparable both in volume and complexity. In short, human intervention would simply bog down the exchange of very deep and broad knowledge elements. | ||
The FaceBook AI agents "Bob" and "Alice" were AI agents that Facebook developed several years ago. They developed a private language that it used to communicate with each other. They were programmed to negotiate the purchase and sale of various items. '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.cnbc.com/2017/08/01/facebook-ai-experiment-did-not-end-because-bots-invented-own-language.html Bob and Alice - FaceBook]''''' technical staff discovered this they found it surprising and unnerving. This was because the agents optimized their behavior such that they created their own '''''short hand''''' to expresses various imperatives or interrogatives. | The FaceBook AI agents "Bob" and "Alice" were AI agents that Facebook developed several years ago. They developed a private language that it used to communicate with each other. They were programmed to negotiate the purchase and sale of various items. '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.cnbc.com/2017/08/01/facebook-ai-experiment-did-not-end-because-bots-invented-own-language.html Bob and Alice - FaceBook]''''' technical staff discovered this they found it surprising and unnerving. This was because the agents optimized their behavior such that they created their own '''''short hand''''' to expresses various imperatives or interrogatives. | ||
| Line 110: | Line 110: | ||
The following table suggests a very simplified diagrammatic summarization of how we could see something like Zoom taken into a higher dimensional space. | The following table suggests a very simplified diagrammatic summarization of how we could see something like Zoom taken into a higher dimensional space. | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Prototype Collaborative Cognition (2023).: </SPAN>''''' Based upon socio-cultural modeling and analysis (socioeconomic, political, geopolitical interaction analysis using multi-agent environments); a group of researchers at Stanford University and Google recently published a paper on how they created a version of the popular Sim World game. They created an artificial village with twenty five “inhabitants”. Each of these “inhabitants” or agents possessed motives, background and history, interior monologs and were able to create new goals as well as interact with each other; the results were startling; a significant development was that the system exhibited emergent properties that the developers had not originally expected; looking forward we can expect that these kinds of artificial environments will proliferate and improve their sophistication, often with a range of unexpected emergent properties; | ||
We should expect to see an intelligent interface control protocol that resembles those found with pen tablet or otherwise touch screen capabilities. A baseline approach that might suggest a way forward can be seen with the Cintiq line of pen tablet devices. | We should expect to see an intelligent interface control protocol that resembles those found with pen tablet or otherwise touch screen capabilities. A baseline approach that might suggest a way forward can be seen with the Cintiq line of pen tablet devices. | ||
| Line 318: | Line 318: | ||
[[File:CG4EnsembleIF01.jpeg|right|560px|Society of Mind]] | [[File:CG4EnsembleIF01.jpeg|right|560px|Society of Mind]] | ||
We can envision teams of individuals working collaboratively together producing results in real time in response to rapidly shifting public perceptions; they might be co-located or geographically dispersed; in the example shown above they might be using high performance pointing devices to control sophisticated Deep Mind processing; <BR /> | We can envision teams of individuals working collaboratively together producing results in real time in response to rapidly shifting public perceptions; they might be co-located or geographically dispersed; in the example shown above they might be using high performance pointing devices to control sophisticated Deep Mind processing; </BR></BR> | ||
'''''< | '''''<Span Style="COLOR:BLUE;BACKGROUND:SILVER">Development Path.</SPAN>''''' Looking forward we will very likely see ensembles of agents much like the society that the Google and Stanford team created resulted in a small village with twenty five “inhabitants”. Each of these “inhabitants” were GPT based agents. Each agent possessed motives, background and history, interior monologs. A team might act as the high level interface to a very large ensemble of CP's; these could range up into the hundreds or thousands. | ||
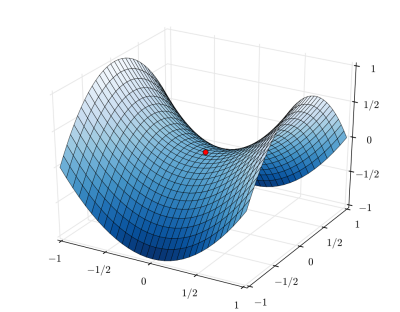
[[File:MiniMax.png|left|400px|Optimization Across Multiple Variables]] | [[File:MiniMax.png|left|400px|Optimization Across Multiple Variables]] | ||
They were able to pursue goals either individually or collectively. They are able to create new episodic memories which can be used to compare the results of recent events to existing goals. In the process they were able to self-improve their performance. As the model played itself forward some surprising and starling results became evident. What happened was that the system gradually began to exhibit emergent properties that the developers had not originally expected. This suggests that arriving at a desired solution might involve navigating a multidimensional space with a variety of peaks and valleys. In short, the more interesting problems will not have a direct linear path to their identification. | They were able to pursue goals either individually or collectively. They are able to create new episodic memories which can be used to compare the results of recent events to existing goals. In the process they were able to self-improve their performance. As the model played itself forward some surprising and starling results became evident. What happened was that the system gradually began to exhibit emergent properties that the developers had not originally expected. This suggests that arriving at a desired solution might involve navigating a multidimensional space with a variety of peaks and valleys. In short, the more interesting problems will not have a direct linear path to their identification. If we look forward a bit then we should expect that these kinds of cognitive environments will proliferate and improve their sophistication, often with a range of unexpected emergent properties. Further, we should expect to see heretofore unexpected emergent behavior.<BR /></BR> | ||
'''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.youtube.com/watch?v=-pb3z2w9gDg&ab_channel=MITOpenCourseWare Society of Mind].</SPAN>''''' A recent effort by teams from Google and Stanford University demonstrated how socio-cultural modeling and analysis was described in a recently published a paper. Their analysis was very similar in its operation to the popular PC Sim World game. (Note: Society of Mind was a book written by Professor Marvin Minsky (MIT) which explored how the brain’s neurons organized themselves into collections to perform specific tasks. In short, he viewed the brain as a society of minds). What these recent Stanford and Google researchers have done is to have created a “micro” version of what Minsky was proposing. In this case however the agents represent elements of a society. | |||
If we look forward a bit then we should expect that these kinds of cognitive environments will proliferate and improve their sophistication, often with a range of unexpected emergent properties. Further, we should expect to see heretofore unexpected emergent behavior.<BR /> | |||
[[File:MiniMax01.png|left|450px|Optimization]] | [[File:MiniMax01.png|left|450px|Optimization]] | ||
A logical next step will be the enablement of each individual to have their own CG4 (CG5?) instance available and accessible to all participants such that these instances can perform real time exchanges. When this happens then we should expect to see a proliferation and explosion of what might be described as a "composite mind". In this instance we might see situations where interacting CG4 instances were only able to communicate with each other during a live session. In other instances these might be taking place asynchronously between participants. Obviously this means that the same '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.wikiwand.com/en/Metcalfe%27s_law Metcalf power law]</SPAN> that applies to networks will apply to these collections of "minds". The greater the number of nodes on a network the more valuable it becomes. | A logical next step will be the enablement of each individual to have their own CG4 (CG5?) instance available and accessible to all participants such that these instances can perform real time exchanges. When this happens then we should expect to see a proliferation and explosion of what might be described as a "composite mind". In this instance we might see situations where interacting CG4 instances were only able to communicate with each other during a live session. In other instances these might be taking place asynchronously between participants. Obviously this means that the same '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.wikiwand.com/en/Metcalfe%27s_law Metcalf power law]</SPAN>''''' that applies to networks will apply to these collections of "minds". The greater the number of nodes on a network the more valuable it becomes. | ||
This seems to be a logical and plausible next step in the further refinement and usage of tools such as CG4 will be collaborative environments. These kinds of collaborations can be envisioned as consisting multiple simultaneous users. Operationally this form of collaboration would bear a strong resemblance to a WEBEX or Zoom call. | This seems to be a logical and plausible next step in the further refinement and usage of tools such as CG4 will be collaborative environments. These kinds of collaborations can be envisioned as consisting multiple simultaneous users. Operationally this form of collaboration would bear a strong resemblance to a WEBEX or Zoom call. | ||
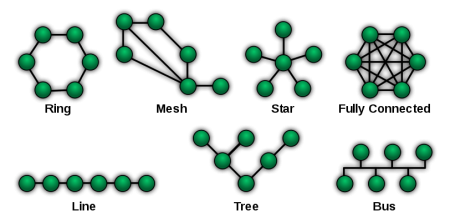
Participants might participate online in real time. They would ''wire'' together their various instantiations of CG4 together into a network. This network could utilize any of the standard forms of connectivity (B*Tree, mesh, ring, bus, star); each agent might act either under direction of its owner or it can act autonomously. The result would be a composite entity. The would result in a new reality wherein '''''< | Participants might participate online in real time. They would ''wire'' together their various instantiations of CG4 together into a network. This network could utilize any of the standard forms of connectivity (B*Tree, mesh, ring, bus, star); each agent might act either under direction of its owner or it can act autonomously. The result would be a composite entity. The would result in a new reality wherein '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">the whole would be greater than the sum of its parts</SPAN>'''''. CG4 can establish a linkage to the IBM Watson system via the IBM Watson API. '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[[IBM.Watson.API|IBM Watson API]].</SPAN>''''' | ||
[[File:NetworkTopology02.png|left|450px|Conformal Mapping Topology Elements]] | [[File:NetworkTopology02.png|left|450px|Conformal Mapping Topology Elements]] | ||
| Line 340: | Line 338: | ||
This stepping forward to computationally mediated communication introduces novel possibilities. For instance one can envision an model wherein all participants use the same CG4, in another instance the processing elements might be heterogeneous. Currently the other major knowledge based artificial intelligence system that can be directly access via its API is the IBM Watson Studio. | This stepping forward to computationally mediated communication introduces novel possibilities. For instance one can envision an model wherein all participants use the same CG4, in another instance the processing elements might be heterogeneous. Currently the other major knowledge based artificial intelligence system that can be directly access via its API is the IBM Watson Studio. | ||
In other settings one might see the use of | In other settings one might see the use of '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://cloud.ibm.com/developer/watson/dashboard IBM Watson] </SPAN>''''' or some comparable variant; judging from the pace of progress we deem this to be a very high probability, high value/payoff approach; because of the flexibility of interconnectivity and interoperability this model can scale to arbitrary size; | ||
This is just an example, and the specific methods you use will depend on which part of the Watson API you're interfacing with. The Watson API provides many different services, including natural language understanding, speech-to-text, text-to-speech, visual recognition, and more. | This is just an example, and the specific methods you use will depend on which part of the Watson API you're interfacing with. The Watson API provides many different services, including natural language understanding, speech-to-text, text-to-speech, visual recognition, and more. | ||
| Line 354: | Line 352: | ||
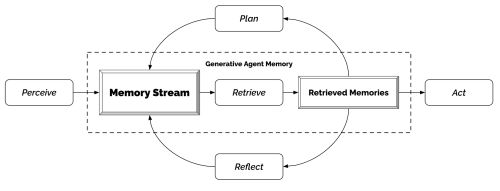
Working from the work done by the Google and Stanford team that created the Agent Sim environment we can imagine that a serious working system might extend beyond a 'plan/reflect' loop. Other factors might be incorporated beyond this simplified version. | Working from the work done by the Google and Stanford team that created the Agent Sim environment we can imagine that a serious working system might extend beyond a 'plan/reflect' loop. Other factors might be incorporated beyond this simplified version. | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Political Action.</SPAN>''''' | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Sentiment Analysis.</SPAN>''''' The British company Cambridge Analytica became well known through its ability to analyze voter sentiment across a broad range of topic and hot button issues; it excelled at creating highly specific messaging to remarkably small target groups that led to decisions to vote or not vote on specific issues; | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Preemptive Campaigns.</SPAN>''''' Existing analysis tools such as sentiment analysis will become increasingly sophisticated; as the do we should expect that they will be applied to public figures, especially legislators and others in positions of influence; these insights might be based upon public actions; in the case of politicians voting records, position papers and constituency analysis will be at the forefront of study; | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Subversion.</SPAN>''''' | ||
[[File:OPMbreach.jpg|left|550px|Office of Personnel Breach (All US Government Security Holders]] | [[File:OPMbreach.jpg|left|550px|Office of Personnel Breach (All US Government Security Holders]] | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Personal Compromise.</SPAN>''''' Access to detailed information about information about individuals of interest such as those with national security or defense related clearances will be favorite targets of malicious actors; the recent attack on the Office of Personnel Management is a foretaste of what is to come; by gaining access to information about individuals with highly sensitive clearances a foreign actor can position themselves to compromise, threaten or otherwise coerce specific individuals with clearances or people who are directly or indirectly related or associated with them; | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Extortion.</SPAN>''''' The Office of Personnel Management of the US Government was hacked by PRC hackers. The result was the capture of millions of profiles of US citizens with security clearances. Possession of the details of these individuals puts them at considerable risk. Risk factors include: knowing where they work and what programs they have access to, data on relatives, co-workers, detailed identification information suitable for creating false credentials. | ||
Counter Intelligence specialists have over years identified four major reasons that motivate a person in a trusted position to betray their trust. These four reasons are summarized as '''''MICE: M: Money I: Ideology C: Compromise E: Ego''''' | Counter Intelligence specialists have over years identified four major reasons that motivate a person in a trusted position to betray their trust. These four reasons are summarized as '''''MICE: M: Money I: Ideology C: Compromise E: Ego''''' | ||
Foreign agencies are constantly on the lookout for targets of opportunity that can be be willing or unwittingly compromised. Once they have been identified it is then a matter of identifying a pathway to an encounter that would enable capture. | Foreign agencies are constantly on the lookout for targets of opportunity that can be be willing or unwittingly compromised. Once they have been identified it is then a matter of identifying a pathway to an encounter that would enable capture. | ||
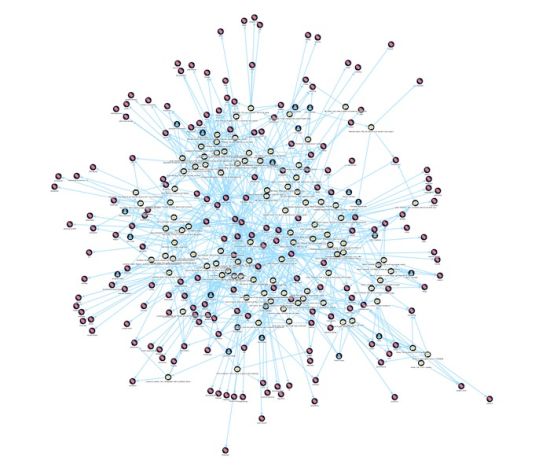
One of the biggest data breaches occurred in 2015. The Office of Personnel Management had an unknown amount of extremely sensitive information about all government employees with a security clearance. This breach can have consequences lasting for years or longer. In the diagram below a dense network of connection is evident. In most cases a given individual will have no idea of the other people who are in that network of connections. They may never encounter any of them or know any of them. The degrees of separation specify how many introductions are required in order to bring one individual in the network into direct or close if indirect contact with a target. Typically this will be five or often less. | One of the biggest data breaches occurred in 2015. The Office of Personnel Management had an unknown amount of extremely sensitive information about all government employees with a security clearance. This breach can have consequences lasting for years or longer. In the diagram below a dense network of connection is evident. In most cases a given individual will have no idea of the other people who are in that network of connections. They may never encounter any of them or know any of them. The degrees of separation specify how many introductions are required in order to bring one individual in the network into direct or close if indirect contact with a target. Typically this will be five or often less. | ||
| Line 376: | Line 373: | ||
The current reality of massive online databases detailing stunningly detailed information on nearly everyone alive within a nation means that the ability to capture this data and use it against the target nation is very great. With a deep learning system the risks eclipse those that have existed in the past. This obtains from the fact that it is now possible to create very detailed plans of action that would enable gaining access to a desired target individual. By using information captured from one or more of the major credit agencies then identifying and maneuvering a compromised individual becomes orders of magnitude easier than in the past. | The current reality of massive online databases detailing stunningly detailed information on nearly everyone alive within a nation means that the ability to capture this data and use it against the target nation is very great. With a deep learning system the risks eclipse those that have existed in the past. This obtains from the fact that it is now possible to create very detailed plans of action that would enable gaining access to a desired target individual. By using information captured from one or more of the major credit agencies then identifying and maneuvering a compromised individual becomes orders of magnitude easier than in the past. | ||
Possession of this type of information can enable an adversary to be highly selective in targeting prospective individual who might be susceptible to compromise, blackmail or being suborned otherwise. An attack vector could be via a direct path or could involve threatening or intimidating a family member. The possibilities are endless. | Possession of this type of information can enable an adversary to be highly selective in targeting prospective individual who might be susceptible to compromise, blackmail or being suborned otherwise. An attack vector could be via a direct path or could involve threatening or intimidating a family member. The possibilities are endless. | ||
| Line 388: | Line 384: | ||
In another scenario they might be on an elevator in a tall building. Seemingly, spontaneously the elevator might halt between floors for many minutes or much longer. The upshot being that the target individual could miss a flight. Add in that wireless telephone service could also be disabled for that immediate locus. Effectively putting that person out of contact. | In another scenario they might be on an elevator in a tall building. Seemingly, spontaneously the elevator might halt between floors for many minutes or much longer. The upshot being that the target individual could miss a flight. Add in that wireless telephone service could also be disabled for that immediate locus. Effectively putting that person out of contact. | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Molecular Modeling.</SPAN>''''' | ||
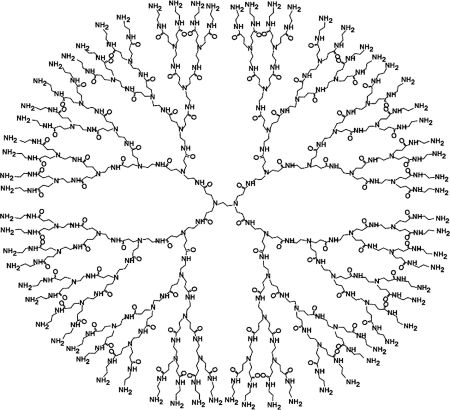
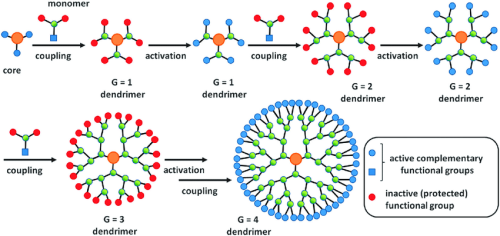
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Tool or Weapon.</SPAN>''''' A committed agency or group can use a tools such as CG4 to refine molecular models to accomplish specific purposes. For instance the developing field of polymer dendrimer molecules enable the possibility of creating molecular structures with heretofore unimagined capabilities. By way of summary, a dendrimer molecule is a specific type of molecule that consists of a series of layers. Structurally they loosely resemble an onion. | ||
'''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Dendrimer Molecules.</SPAN>''''' Relatively recent developments in molecular design have brought to light molecules that can be layered. Dendrimer molecules can be used for a variety of purposes such as the creation of substances with very novel features. Surfactants can be constructed that offer hydrophobic behavior. Other dendrimer structures can be used for '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.youtube.com/watch?v=-25WHokUOI8&ab_channel=MichaelBeigel drug delivery].</SPAN>''''' A keen observer will note that this technology can be used for both ethical, constructive purposes as well as non-ethical purposes. The range of potential uses is sufficiently broad that a catalog of possibilities would be very difficult to articulate. | |||
[[File:dendrimer03.jpg|left|450px|Targeted Synthetic Multilayered Molecules]] | [[File:dendrimer03.jpg|left|450px|Targeted Synthetic Multilayered Molecules]] | ||
| Line 404: | Line 399: | ||
Notice in the following diagram that one can see the progressive stages involved in constructing a dendrimer molecule; by stage three we can see how payload voids have become available; it then becomes possible to mount highly refined and specific molecules into these voids; depending upon the embedding layers we can determine how, when and under what conditions the payload will be released; by generation 4 one can recognize that a prior payload has voids available for other molecules; | Notice in the following diagram that one can see the progressive stages involved in constructing a dendrimer molecule; by stage three we can see how payload voids have become available; it then becomes possible to mount highly refined and specific molecules into these voids; depending upon the embedding layers we can determine how, when and under what conditions the payload will be released; by generation 4 one can recognize that a prior payload has voids available for other molecules; | ||
As of July 2023 '''''<Span Style="COLOR:BLUE;BACKGROUND:YELLOW">[https://www.ncbi.nlm.nih.gov/pmc/articles/PMC3638248/pdf/nihms455948.pdf thirteen generation dendrimer molecules]</SPAN>''''' have been successfully fabricated. | As of July 2023 '''''<Span Style="COLOR:BLUE;BACKGROUND:YELLOW">[https://www.ncbi.nlm.nih.gov/pmc/articles/PMC3638248/pdf/nihms455948.pdf thirteen generation dendrimer molecules]</SPAN>''''' have been successfully fabricated. | ||
Below we can see a more symbolic representation of how many different payload molecules can be imbedded within a dendrimer molecule; the result is that there is a very large range of possibilities; | Below we can see a more symbolic representation of how many different payload molecules can be imbedded within a dendrimer molecule; the result is that there is a very large range of possibilities; | ||
| Line 424: | Line 417: | ||
In related news, Integrated Biosciences, the Broad Institute (MIT) and Harvard used a deep learning system to screen 800000 chemical compounds. | In related news, Integrated Biosciences, the Broad Institute (MIT) and Harvard used a deep learning system to screen 800000 chemical compounds. | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Novel Psycho Actives.</SPAN>''''' Dendrimer technology can be used to fabricate combinations of pharmaceutical substances for highly specific and focused effects. Were an agency or group to decide to use a tools such as CG4 to design a novel molecular structure then it does no seem to be out of the realm of reality that the most sophisticated combinations of molecular structures could be designed and delivered to a target; because these are at molecular scale they could be made to be effectively undetectable; they could be made to react to various environmental conditions or activate based upon a time release scheme; further they can be made to use the same payloads but have these payloads released at varying intervals; the possibilities are limitless; | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Targeted Bioweapons.</SPAN>''''' The ability to synthesize and model new molecular structures will be hastened with tools such as CG4; the rival company Deep Mind recently supported the effort to arrive at a SARS COVID-19 vaccine; the company used its Deep Fold 2 system to screen millions of possible vaccine molecular structures; the result was that it arrived at a small set of viable candidate molecular structures in a matter of days; equally possible would be molecular structures that were capable of causing debilitating physiological or psychological functioning; | ||
[[File:dendrimer02.jpg|center|400px|Complex Molecular Payload Dendrimer]] | [[File:dendrimer02.jpg|center|400px|Complex Molecular Payload Dendrimer]] | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Carbon Nanotubes.</SPAN>''''' These are novel molecules with extremely regular lattice-like structures. They can be used to fabricate materials with novel properties. These properties can be targeted to result in materials of extremely high tensile strength, filtering capabilities and innumerable other specific applications. | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Inorganic (materials, pharmaceuticals such as dendrimer, mono-filament molecules) </SPAN>'''''such as: | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Room Temperature Superconducting Materials.</SPAN>''''' Such a development would revolutionize societies in ways that cannot be fully characterized; another usage of such a capability might be in the fabrication of power storage capabilities; these forms of molecular combinations could result in storage batteries with power densities hundreds or thousands of times beyond those currently available; a battery the size of a loaf of bread might be capable of storing sufficient power to operate a standard home with all of its devices operating for days, weeks or longer; | ||
[[File:ctubes00.jpg|left|400px|Carbon Nanotube]] | [[File:ctubes00.jpg|left|400px|Carbon Nanotube]] | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Extremely High Tensile Strength Materials.</SPAN>''''' These might be derivatives of carbon nanotube material; but with much higher tensile strength; fibers made out of such material can be used as a saw blade; strands and weaves of such material could be used as a space elevator material; other uses might be in the use of nearly impervious shields such as bullet proof vests if woven into a fabric-like material and covered such that it did not endanger the wearer; | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Organic (Biological) Modeling Capabilities.</SPAN>''''' This can include a variety of structures(proteins, enzymes, hormones virus, bacteria, prions) The identification of molecular structures that enable the interdicting of metabolic failure can be envisaged. This could mean that new tools can emerge that go beyond the already remarkable CRISPR-CAS9 model and its derivatives. One can envision the creation of variants of molecular substances that mimic the hemoglobin molecule found in certain reptiles such as alligators or whales. These animals routinely demonstrate the ability to remain submerged for many minutes on end without resorting to returning to the surface to breathe. | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Combined Novel Molecular Modeling Capabilities.</SPAN>''''' New multipurpose materials(substances, pharmaceuticals). These materials may be the result of combining organic and inorganic molecular structures to arrive at a result with heretofore novel and unexpected properties and capabilities; | ||
In recent weeks an awareness has begun to rapidly crystalize an awareness of the possibility of dual use molecular design and synthesis. The recent reporting that focused on Combinations Pharmaceuticals is a case in point. In this case the company fabricated its own deep learning tool. Its primary focus and cause for existence was and is for the discovery of viable, safe and useful pharmaceutical drugs. | In recent weeks an awareness has begun to rapidly crystalize an awareness of the possibility of dual use molecular design and synthesis. The recent reporting that focused on Combinations Pharmaceuticals is a case in point. In this case the company fabricated its own deep learning tool. Its primary focus and cause for existence was and is for the discovery of viable, safe and useful pharmaceutical drugs. | ||
| Line 446: | Line 439: | ||
Their discovery that deep learning neural networks could be used to facilitate search prompted management to opt for a targeted system capable of learning about how molecular compounds are structured. After a period of training their MegaSym system was dispatched to search for promising drug candidates for various purposes. On a whim their chief researcher Dr Urbani decided to flip the value associated with toxicity from a zero to a minus one. The result was that within six hours the deep learning system had generated a list of approximately 40000 chemical substances. In many cases the results were far more lethal and toxic than VX. A bit more on this momentarily. | Their discovery that deep learning neural networks could be used to facilitate search prompted management to opt for a targeted system capable of learning about how molecular compounds are structured. After a period of training their MegaSym system was dispatched to search for promising drug candidates for various purposes. On a whim their chief researcher Dr Urbani decided to flip the value associated with toxicity from a zero to a minus one. The result was that within six hours the deep learning system had generated a list of approximately 40000 chemical substances. In many cases the results were far more lethal and toxic than VX. A bit more on this momentarily. | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Novel Protein Design.</SPAN>''''' Recent developments in using deep learning systems has been the emergence of protein designs that are 'made to order'. These are protein structures whose properties a protein designer can specify. Within minutes the design software, known as '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.nature.com/articles/d41586-023-02227-y RFdiffusion]</SPAN>''''' is able to offer molecular structures for review. It is now available as an open source software tool. | ||
It is not far fetched to consider that this tool can be used for purposes that might have been considered science fiction just a few years ago. A case in point might be using a variant of this RFDiffusion tool to devise a variation on the human hemoglobin molecule such that it has substantially greater oxygen retention capacity. Mammals such as dolphins and whales might reveal ways in which their hemoglobin might be adapted for human purposes. | It is not far fetched to consider that this tool can be used for purposes that might have been considered science fiction just a few years ago. A case in point might be using a variant of this RFDiffusion tool to devise a variation on the human hemoglobin molecule such that it has substantially greater oxygen retention capacity. Mammals such as dolphins and whales might reveal ways in which their hemoglobin might be adapted for human purposes. | ||
| Line 455: | Line 448: | ||
In other uses it is now possible to genetically splice traits from one species into the DNA of another. In recent years progress has shown that the enzyme known as luciferase can be spliced from firefly DNA into the DNA segment responsible for skin coloration. The result is that one can now have animals that glow in the dark. | In other uses it is now possible to genetically splice traits from one species into the DNA of another. In recent years progress has shown that the enzyme known as luciferase can be spliced from firefly DNA into the DNA segment responsible for skin coloration. The result is that one can now have animals that glow in the dark. | ||
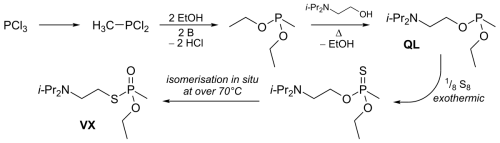
'''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">Synthetic Molecule Design. | '''''<Span Style="COLOR:BLUE;BACKGROUND:YELLOW">Synthetic Molecule Design. ([https://pubs.acs.org/doi/pdf/10.1021/acsomega.2c01404 MegaSyn]</SPAN>''''' VX Ekins Urbina North Carolina) Recent work at the University of North Carolina in collaboration with a private firm known as '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.collaborationspharma.com/megasyn Collaborations Pharmaceuticals].</SPAN>''''' resulted in a list of approximately 40000 chemical structures with known toxic to extremely toxic properties. | ||
[[File:VX00.png|left|500px|Synthetic Nerve Agent Molecular Structure]] | [[File:VX00.png|left|500px|Synthetic Nerve Agent Molecular Structure]] | ||
| Line 466: | Line 459: | ||
[[File:limitless.jpeg|left|400px|Cognitive Enhancement]] | [[File:limitless.jpeg|left|400px|Cognitive Enhancement]] | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Novel Targeted Pharmaceutical Enhancement Design.</SPAN>''''' In the movie 2011 movie '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.wikiwand.com/en/Limitless_(film) Limitless]</SPAN>''''' a wannabe author encounters an acquaintance of his while walking through Manhattan. The acquaintance passes him a small packet of tablets and suggests how they might help. It turns out that when used properly they provide the user with perfect recall. The effect that the nootropic is almost immediate. An individual who has ingested a small dosage is able to harness their ability to control both short and long term recall far beyond what is currently possible. Looking forward researchers may identify a means whereby the synthesis of selective activators as the fictional NZT-48 might become available. | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Societally Disruptive Memory Enhancement.</SPAN>''''' If we look forward a short distance we believe that there will be an emergence of gray market products and services that will restructure the world view of most Western societies.<BR /> These kinds of developments have been well known in prior eras. During the era known as Prohibition in the US in the 1920's and 1930's alcohol was prohibited from sale. The result was that alcohol black markets emerged. That this was so derived simply because there was an ongoing and persistent demand. So, where there was a demand, enterprising individuals found ways to either produce alcoholic based drinks or to smuggle it into the US. The result was that there was a huge market for black market alcohol and establishments where it could be bought and consumed.<BR /> | ||
[[FILE:BTCN00.jpeg|right|400px|BitCoin|BitCoin Anonymous Exchange]] | [[FILE:BTCN00.jpeg|right|400px|BitCoin|BitCoin Anonymous Exchange]] | ||
| Line 479: | Line 472: | ||
It would operate along the following lines: | It would operate along the following lines: | ||
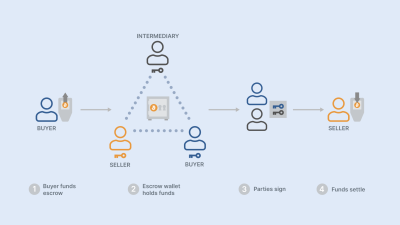
*'''''< | *'''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">BitCoin Account.</SPAN>''''' A prospective client or customer would gain anonymity by establishing a BitCoin account. | ||
*'''''< | *'''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">BitCoin Escrow Account.</SPAN>''''' Verification of a transaction will require the services of a neutral but reputable third party. | ||
*'''''< | *'''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Precursor Supplier.</SPAN>''''' The supplier would need to be able to post notice of the range of available choices. | ||
*'''''< | *'''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Anonymous Logistics.</SPAN>''''' Receipt of the semi-finished product would be expedited by having an anonymous logistic point. The American logistics company named United Parcel Service (UPS) or an enterprise providing similar capabilities would suffice. It is not unusual to be able to find a UPS store. A service of these facilities are the equivalent of numbered post office boxes. Once an order has been fulfilled and delivered the customer can be notified that it is ready for pickup and the supplier can be paid thus completing the transaction. In the range of actions anonymity is maintained. | ||
**'''''< | **'''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Customer Purchase Order (CPS).</SPAN>''''' A purchaser would select the specific end result molecular structure. This would be sent as an encrypted request to a known, reliable and reputable precursor pharmaceutical provider. | ||
**'''''< | **'''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER"> Chemistry Precursor Supplier (CPS).</SPAN>''''' The pharmaceutical synthesist would accept the request, acknowledge its receipt and issue a detailed invoice. This invoice would specify the precursor elements and the relative dosages and steps needed to produce the finished product. | ||
**'''''< | **'''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Bitcoin Account (BA).</SPAN>''''' Each party would use Bitcoin as a means of payment. In order to proceed with the delivery the supplier would query a BES to verify that payment had been made. | ||
**'''''< | **'''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Chemistry Precursor Validator (CPV).</SPAN>''''' This is an independent third party selected by the Customer. The role of this party would be to validate the reputation of the CPS for any questionable activities or irregularities. The CPS would have delivered to the CPV very small quantities to test and verify that they were what they were claimed to be. | ||
**'''''< | **'''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Bitcoin Escrow Service (BES).</SPAN>''''' After payment had been made and the product precursor elements assembled, these would be presented to a second BES. This second CPV actor would then signal to the Customer that the shipment was what it was claimed to be. At this point the BES would authorize payment release to the CPS and shipment to the Customer. | ||
** ''''' < | ** '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Anonymous Logistics</SPAN>''''' After the elements had been shipped then an AL facility would receive them. On receipt the AL would be able to notify the box holder of the arrival of a shipment to be collected. The anonymous box holder would then collect the items and signal to the supplier that receipt had been completed. Thus closing the transaction. | ||
[[FILE:BTCN03.png|left|400px|BitCoin Escrow Anonymous Confirmation Service]] | [[FILE:BTCN03.png|left|400px|BitCoin Escrow Anonymous Confirmation Service]] | ||
| Line 519: | Line 512: | ||
[[File:zanzibar.jpeg|right|250px|John Brunner 1968 predictions for 2014]] | [[File:zanzibar.jpeg|right|250px|John Brunner 1968 predictions for 2014]] | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Eptification.</SPAN>''''' The 1968 novel '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.wikiwand.com/en/Stand_on_Zanzibar Stand On Zanzibar]</SPAN>''''' by John Brunner broached the possibility of facilitating highly specific and targeted long and short term recall using pharmaceutical means. In the novel a character named Donald Hogan is a PhD in biology. He has been on military reserve status for some number of years. He suddenly discovers that he has been activated and is given instruction to report to a nearby military facility. The location is innocuous but is highly secure. While there he is subjected to a process known as ''eptification''; He is trained in a variety of subjects one of which is extremely lethal hand to hand combat; his training time is surprisingly brief; however on completion he discovers that he is able to recall things that he has written with amazing clarity. Modern day techniques comparable to those used by the MegaSyn system could well sketch out a pathway to the synthesis of something along the lines of NZT-48. | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Social Engineering.</SPAN>''''' Our perception is that unexpected and novel social developments and processes can be set in motion and managed over time. A catchall heading for these kinds of endeavors might be the category of "social engineering" for lack of a better way to identify a catch-all. Social engineering might result in emitting messages within a social sphere with the intent of motivating and activating various groups or collections of people; in this case the individuals themselves might or might not even realize that they are being manipulated. | ||
A CG4 category tool can be used to create models of social processes; these processes can then be characterized in terms of how various groups respond to select social messages and signals. | A CG4 category tool can be used to create models of social processes; these processes can then be characterized in terms of how various groups respond to select social messages and signals. | ||
| Line 531: | Line 524: | ||
An example of this kind of situation can be seen in the Great Lakes of North America where the Asian Carp has invaded several of the waterways. They have proven to be a voracious predator and have crowded out the other native species. In order to mitigate their presence and associated risks conservation teams have had to resort to concerted efforts to halt their advance. Some approaches have involved dropping netting across waterways. Another approach has been to use electric shock fences to turn them back. | An example of this kind of situation can be seen in the Great Lakes of North America where the Asian Carp has invaded several of the waterways. They have proven to be a voracious predator and have crowded out the other native species. In order to mitigate their presence and associated risks conservation teams have had to resort to concerted efforts to halt their advance. Some approaches have involved dropping netting across waterways. Another approach has been to use electric shock fences to turn them back. | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Secret Life of Plants.</SPAN>''''' '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.ted.com/talks/suzanne_simard_how_trees_talk_to_each_other Recent botanical research]''''' has revealed that stands of trees form incredibly dense communications networks through their root systems. They use these root systems to exchange nutrients and messages. They have revealed themselves to be surprisingly robust in exchanging environmental messaging as well. In the event of an invasion attempt by a predatory or parasitic species they are able to signal each other to release toxins as a means to ward off these forms of attacks. | ||
A lesson learned in trying to deal with this problem has been that they exhibit peculiar habits such as becoming very evident and active at certain times of day. Champions for their presence have shown that by emitting a certain pitch at these times of day will cause them to congregate in certain parts of a waterway. This congregation behavior can cause interruptions in the regular flow of events. In some cases these interruptions are mild and can be ignored. In other cases when serious fishery activities are at hand these can be very disruptive. An approach is recommended that would enable minimizing and ultimately removing this burdensome and irritating presence. | A lesson learned in trying to deal with this problem has been that they exhibit peculiar habits such as becoming very evident and active at certain times of day. Champions for their presence have shown that by emitting a certain pitch at these times of day will cause them to congregate in certain parts of a waterway. This congregation behavior can cause interruptions in the regular flow of events. In some cases these interruptions are mild and can be ignored. In other cases when serious fishery activities are at hand these can be very disruptive. An approach is recommended that would enable minimizing and ultimately removing this burdensome and irritating presence. | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Industry Models.</SPAN>''''' Targeted Industry Segment Analysis – identification of bottlenecks, weak links, possible disruption points. | ||
[[File:BizProcess03.jpg|left|400px|Ultra High Resolution Process Modeling]] | [[File:BizProcess03.jpg|left|400px|Ultra High Resolution Process Modeling]] | ||
| Line 541: | Line 534: | ||
Using CG4 it becomes possible to model a business process in arbitrary detail. This suggests that it is possible to create models of very fine granular detail. With the appropriate control mechanisms one can study the effects of internal or external events. Such as tool would enable deep understanding about the factors that adversely or positively impact that particular process. Such a capability can be disruptive depending upon how such insight is put to use. | Using CG4 it becomes possible to model a business process in arbitrary detail. This suggests that it is possible to create models of very fine granular detail. With the appropriate control mechanisms one can study the effects of internal or external events. Such as tool would enable deep understanding about the factors that adversely or positively impact that particular process. Such a capability can be disruptive depending upon how such insight is put to use. | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Exploratory Analysis.</SPAN>''''' Existing modeling tools have reached a level of sophistication that major government organizations, universities and think tanks have incorporated these kinds of tools into their bag of tricks. One can envision using a powerful tool such as CG4 to model the processes of a major geopolitical development. Recent news reports (as of June 2023) offer strong indications that the US and the PRC may be heading toward some form of confrontation in the South China Sea littoral. In at one instance a major think tank known as '''''<SPAN Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.youtube.com/watch?v=bFDMh_dyshY&ab_channel=CenterforStrategic%26InternationalStudies CSIS]</SPAN>''''' reported their results of an exploration of events involving a PRC invasion of the island of Taiwan. | ||
According to various reports the results varied from just tolerable to remarkably bad. A tool such as CG4 can clearly be used to model in arbitrary detail the processes that involve multiple agents, a variety of resources and any number of uncertainties, potential bottle necks and other factors that can predispose events to progress in one direction rather than another. | According to various reports the results varied from just tolerable to remarkably bad. A tool such as CG4 can clearly be used to model in arbitrary detail the processes that involve multiple agents, a variety of resources and any number of uncertainties, potential bottle necks and other factors that can predispose events to progress in one direction rather than another. | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Process Modeling: Social, Economic, Political, Geopolitical:</SPAN>''''' selectively focus on global areas of interest; the objective being the creation of tools that enable the operator to “drive” a line of analysis or discourse forward based upon real world limitations, resources, historical realities and current political imperatives; an extension to '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.youtube.com/watch?v=f52FCWb5FEM&ab_channel=CaspianReport Caspian Report]</SPAN>''''' | ||
Modeling commercial or industrial processes can be facilitated by bringing together individuals or sources that possess expertise or data and or knowledge about various aspects of how the target process functions. This means that actual real world processes can be modeled and driven in ways that the actual process and its elements could not. This means that any configuration of loading or overloading can be modeled as a means to stress test the robustness and resilience of the process to withstand unexpected loading. We note that this loading can take the form of being intentionally loaded by those responsible for its functioning or by those whose intent is to disable or destroy it such as an adversary. | Modeling commercial or industrial processes can be facilitated by bringing together individuals or sources that possess expertise or data and or knowledge about various aspects of how the target process functions. This means that actual real world processes can be modeled and driven in ways that the actual process and its elements could not. This means that any configuration of loading or overloading can be modeled as a means to stress test the robustness and resilience of the process to withstand unexpected loading. We note that this loading can take the form of being intentionally loaded by those responsible for its functioning or by those whose intent is to disable or destroy it such as an adversary. | ||
| Line 648: | Line 641: | ||
[[File:geopolitical03.jpg|right|500px|Ultra High Resolution Geopolitical Conflict Analysis Modeling Tool]] | [[File:geopolitical03.jpg|right|500px|Ultra High Resolution Geopolitical Conflict Analysis Modeling Tool]] | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Boundaries Exploration.</SPAN>''''' These might emerge as compelling social, economic, political policy proposals grounded in common sense; possible ways to solve older, existing problems using recent insights into the mechanics, linkages and dynamics of observable processes; | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">New Value Propositions.</SPAN>''''' Near term job market realignment, disruption; (increased social dislocation, disruption). According to the British financial management firm XYZ.PQR source data set information can be provided to CG4 by converting the desired textual material as a .txt file and entering it directly. It can then be preprocessed such that structuring and prompt elements are provided for the system to use to return responses. | ||
Looking forward we can foresee the prospect that a new support sector might emerge that provides rapid knowledge capture and preprocessing services. It would make use of high speed text and image capture. Optical character reading (OCR) capabilities would then render the captured images into processable text. | Looking forward we can foresee the prospect that a new support sector might emerge that provides rapid knowledge capture and preprocessing services. It would make use of high speed text and image capture. Optical character reading (OCR) capabilities would then render the captured images into processable text. | ||
| Line 656: | Line 649: | ||
Isakara Labs in Tokyo demonstrates how their research can capture '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.youtube.com/watch?v=03ccxwNssmo&ab_channel=IshikawaGroupLaboratory 250 book pages of text per minute].</SPAN>''''' One can imagine a small enterprise with a teams of individuals whose tasks would include book capture then conversion to variously text or PDF format for loading into the training data for specific purposes. | Isakara Labs in Tokyo demonstrates how their research can capture '''''<Span Style="COLOR:BLUE; BACKGROUND:YELLOW">[https://www.youtube.com/watch?v=03ccxwNssmo&ab_channel=IshikawaGroupLaboratory 250 book pages of text per minute].</SPAN>''''' One can imagine a small enterprise with a teams of individuals whose tasks would include book capture then conversion to variously text or PDF format for loading into the training data for specific purposes. | ||
[[File:IshBookCap.jpg|left|400px|High Speed Knowledge Text and Image Capture]] | [[File:IshBookCap.jpg|left|400px|High Speed Knowledge Text and Image Capture]] | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Locus of Interest:</SPAN>''''' Emergence of position nexus ecology; crystallization of political polarization; these might be further developments of existing “channels” currently available on youtube.com; but would operate independently of that platform, but become accessible via a “white pages” type structure; | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Food Chain:</SPAN>''''' The emergence of specialist groups dedicated to supporting various actors in the nexus ecology; these will follow existing business development lines with market segmentation and brand identification; we should expect to see emerging markets with offerings that are priced as: high, best, low and niche; | ||
Because of the novelty of these new technologies we should also expect to see the emergence of a set of market places that reflect those found in most commercial settings; this means that there will be; | Because of the novelty of these new technologies we should also expect to see the emergence of a set of market places that reflect those found in most commercial settings; this means that there will be; | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Market Positions by Price - High, Niche, Best, Low:</SPAN>''''' | ||
We should expect to see a rapidly developing market place for new value propositions. These will involve the exchange for ideas, capabilities and services. This marketplace will probably evolve rapidly and shadow the development of the software market place. Initially when there were very few software vendors and the marketplace was perceived to be small then prices for individual software items was substantial. A spreadsheet tool such as Lotus 1-2-3 ran in the hundreds of US dollars. As the marketplace grew prices came down. As perceptions of the size of the marketplace sharpened new products and service providers appeared and the prices gradually fell. We should expect to see a comparable shakeout in the emerging market place of cognitive "fittings", "couplers" and other forms of connectivity. | We should expect to see a rapidly developing market place for new value propositions. These will involve the exchange for ideas, capabilities and services. This marketplace will probably evolve rapidly and shadow the development of the software market place. Initially when there were very few software vendors and the marketplace was perceived to be small then prices for individual software items was substantial. A spreadsheet tool such as Lotus 1-2-3 ran in the hundreds of US dollars. As the marketplace grew prices came down. As perceptions of the size of the marketplace sharpened new products and service providers appeared and the prices gradually fell. We should expect to see a comparable shakeout in the emerging market place of cognitive "fittings", "couplers" and other forms of connectivity. | ||
[[File:MarketPriceMap.jpg|left|500px]] | [[File:MarketPriceMap.jpg|left|500px]] | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Open markets (Official Market)</SPAN>''''' These will be openly and easily accessible and provide buyers and sellers a readily accessible location to enact their exchanges. | ||
What may develop will be a marketplace like any other open, above board marketplace of buyers and sellers. These can be found scattered all over any given major web paged. They often involve being obliged to see and respond to a pop up add in order to view the desired content. | What may develop will be a marketplace like any other open, above board marketplace of buyers and sellers. These can be found scattered all over any given major web paged. They often involve being obliged to see and respond to a pop up add in order to view the desired content. | ||
| Line 671: | Line 664: | ||
What will also shadow this open marketplace will be gray and black market places wherein items are available for exchange that have not yet received full sanction of the host society. | What will also shadow this open marketplace will be gray and black market places wherein items are available for exchange that have not yet received full sanction of the host society. | ||
'''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Recognized Unofficial Markets (gray market).</SPAN>''''' These can be expected to be venues in which are in unregulated venues; they might be located geographically anywhere on the planet; | |||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Covert Markets (black market).</SPAN>''''' we should expect that these venues will function as they always have; unregulated and very much caveat emptor; | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Some Talking Points.</SPAN>''''' Following are a few talking point topics that might serve as a point of entre into the discussion of what kinds of risks CG4 and its variants might pose. We recognize that risks might manifest from malicious actors, systemically and organically or, by way of speculation, using our insight and knowledge about how earlier technologies required regulation and management. We recognize that control of these new technologies may be required insofar as the benefit that they offer might outweigh the downsides of their use. | ||
As in prior technologies there may be the need to demand licensing, registration or other forms of regulation. In the meantime we recognize the reality that human nature has shown itself to be immutable across the span of written history. Therefore we should expect that even if some form of regulation or licensing emerges with this technology there will always be so-called "black markets". The talking points that follow defer discussions of moral imperatives but instead focus upon the possible, knowing what we know about the realities of human behavior. They therefore serve only as a means to spotlight the more obvious uses that this emerging technology might come to light. | As in prior technologies there may be the need to demand licensing, registration or other forms of regulation. In the meantime we recognize the reality that human nature has shown itself to be immutable across the span of written history. Therefore we should expect that even if some form of regulation or licensing emerges with this technology there will always be so-called "black markets". The talking points that follow defer discussions of moral imperatives but instead focus upon the possible, knowing what we know about the realities of human behavior. They therefore serve only as a means to spotlight the more obvious uses that this emerging technology might come to light. | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Problem Characteristics. </SPAN>'''''(these need a) a sanity-check b) another consistency pass, find the center of gravity and redistribute focus accordingly); | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Perceptions.</SPAN>''''' {Provocations False-Flag Misdirection Compromise } | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Beliefs.</SPAN>''''' The major western societies have belatedly discovered that managing perceptions and beliefs has become a major problem. The arrival of broadly accessible social media have created communications environments that can serve up the full range of audio and video content. | ||
And this can all be done with or without any prior vetting, verification or editing; recent developments with tools such as CG4, Dall-E, | And this can all be done with or without any prior vetting, verification or editing; recent developments with tools such as CG4, Dall-E, | ||
| Line 701: | Line 693: | ||
will coalesce into communities of action - with the result that actual "facts on the ground" will shift in possibly sudden and unexpected ways; | will coalesce into communities of action - with the result that actual "facts on the ground" will shift in possibly sudden and unexpected ways; | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Extortion.</SPAN>''''' The Office of Personnel Management breach in 2014 signaled the fact that a broad | ||
swathe of individuals who operate in extremely sensitive roles can be placed at risk overnight; the severity of this breach can not be | swathe of individuals who operate in extremely sensitive roles can be placed at risk overnight; the severity of this breach can not be | ||
overstated because of the fact that in almost all cases the individual who have been identified have had their personal identifying | overstated because of the fact that in almost all cases the individual who have been identified have had their personal identifying | ||
| Line 708: | Line 700: | ||
can then be used as leverage against any of these individuals; | can then be used as leverage against any of these individuals; | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Nano-Scale Fabrication.</SPAN>''''' The ability to fabricate extremely novel pharmaceuticals is palpable. Given that | ||
there are tools available for the creation of molecular structures with remarkable and novel features, traits and characteristics means that | there are tools available for the creation of molecular structures with remarkable and novel features, traits and characteristics means that | ||
the range of possible uses can not be foreseen. The inherent risks associated with the creation of heretofore unheard of or even unimagined | the range of possible uses can not be foreseen. The inherent risks associated with the creation of heretofore unheard of or even unimagined | ||
| Line 734: | Line 726: | ||
Suppose that we postulate the above to be so, we do believe that risks described as theoretical or systemic could come into existence sooner than most observers expect. Therefore we will use this as a staring point. | Suppose that we postulate the above to be so, we do believe that risks described as theoretical or systemic could come into existence sooner than most observers expect. Therefore we will use this as a staring point. | ||
'''''< | '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Risks.</SPAN>''''' {Systemic Malicious Theoretical (SMT)}.<BR> | ||
To list a few that seem to be most imminent and pressing: | To list a few that seem to be most imminent and pressing: | ||
* '''''< | * '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Manufactured or Manipulated Realities and Narratives. </SPAN>''''' | ||
- The ability to craft ultra-realistic messages involving texts, ultra lifelike avatars that make claims about individuals, events or conditions that are not true.<BR> | - The ability to craft ultra-realistic messages involving texts, ultra lifelike avatars that make claims about individuals, events or conditions that are not true.<BR> | ||
- Sentiment manipulation such as that created by Cambridge Analytica.<BR> | - Sentiment manipulation such as that created by Cambridge Analytica.<BR> | ||
- The ability to use and control existing infrastructure (communications, power, civil systems) to cause unplanned outages, wreak chaos, panic and confusion.<BR> | - The ability to use and control existing infrastructure (communications, power, civil systems) to cause unplanned outages, wreak chaos, panic and confusion.<BR> | ||
- The intrinsic pressures involved in an industrial process to adapt the most recent tools and techniques to maintain competitive standing.<BR> | - The intrinsic pressures involved in an industrial process to adapt the most recent tools and techniques to maintain competitive standing.<BR> | ||
*'''''< | *'''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Intrinsic Obsolescence.</SPAN>''''' | ||
- We can see this in strike activities such as the (WGA strike of screen writers) or in other venues.<BR> | - We can see this in strike activities such as the (WGA strike of screen writers) or in other venues.<BR> | ||
- Marginalization of transportation workers through self driving vehicles (automobiles, trucks, busses).<BR> | - Marginalization of transportation workers through self driving vehicles (automobiles, trucks, busses).<BR> | ||
| Line 747: | Line 739: | ||
- Marginalization of educational professionals.<BR> | - Marginalization of educational professionals.<BR> | ||
- Narrowing and steepening of of academic oriented ladders.<BR> | - Narrowing and steepening of of academic oriented ladders.<BR> | ||
*''''' < | *'''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Boosted scientific advances.</SPAN>''''' | ||
- AI designed chemistry, biology, other scientific experiments toward the end of creating new materials, pharmaceuticals and other substances and materials. <BR> | - AI designed chemistry, biology, other scientific experiments toward the end of creating new materials, pharmaceuticals and other substances and materials. <BR> | ||
- Rapid to instant dissemination of research and design information focusing on advanced dual use tools, materials and substances.<BR> | - Rapid to instant dissemination of research and design information focusing on advanced dual use tools, materials and substances.<BR> | ||
* ''''' < | * '''''<Span Style="COLOR:BLUE; BACKGROUND:SILVER">Accelerated domain knowledge refinement and modeling.</SPAN>''''' | ||
- Modeling tools that allow for highly realistic and exquisitely detailed analysis of economic, social, political and geopolitical systems.<BR> | - Modeling tools that allow for highly realistic and exquisitely detailed analysis of economic, social, political and geopolitical systems.<BR> | ||
- Emergence of new market places offering heretofore unavailable pharmaceuticals, processing tools or other forms of control.<BR> | - Emergence of new market places offering heretofore unavailable pharmaceuticals, processing tools or other forms of control.<BR> | ||
Latest revision as of 04:40, 21 July 2024
Overview
Theoretical and Speculative Risks. A review of reports that have emerge in the weeks following the release of Chat GPT4 will show that the number and coverage has proliferated considerably. Attempting to summarize the full impact of this new technology is proving to be a moving target and therefore increasingly difficult to summarize. Several actual or hypothetical examples follow that might serve as starting points for further discussion and analysis. As of June 2023 there has been an explosion of discussions, presentations, documentaries and news reports. These have surfaced in the broader main stream media as well as in the more specialized reporting channels. The result is that those initial topical starting points (listed below) will doubtless be out of date. Therefore the topic obliges revisiting periodically in the upcoming weeks and months.
- Influence and Persuasion. Viewers of Netflix can find on that site a documentary titled The Great Hack (Youtube video links). This documentary details how the company named FaceBook bought a British company named Cambridge Analytica. The documentary details how Cambridge Analytica used access to the massive FaceBook system to categorize eligible voters in both the US and the UK in terms of their political, social and economic values.
Using these insights were able to craft highly specific "hot button" messages to specific voters with the intent to influence voting behavior. These messages were structured such that their true purpose remained obscured.
- Narratives: Highly realistic, plausible narratives and counter-narratives are now effortlessly possible; these might include:
Rumors, Disinformation: we should expect that these narratives will exhibit remarkable saliency and credibility; but in many cases will prove to be groundless; leading the elaboration of this area will probably be the development of divisive social/political narrative creation; i.e. fake news;
Persuasion Campaigns: these might involve recent or developing local issues that residents feel are compelling issues that need addressing but should not wait for the next election cycle to resolve.
The British company RSA Animates has staked out a market niche by offering consistent quality illustrated speeches and lectures. Because of their recognition that many difficult and complex topics can benefit from having an associated sketch illustration that tracks with a speaker's narrative the company has sparked a new industry and has many imitators.
A careful observer will note that the company adheres to a cautious stylistic approach that is calculated to be "middle of the road" or "mainstream". Insofar as it uses sketches of past or present individual the presentation rarely if ever presents them using a caricature approach. We should probably not expect the new wave of animated providers to be so constrained.
Looking forward we should expect to see any number of new companies springing forth that use this same approach but will instead add not only contemporaneous color sketches to support the spoken narrative but rather we should expect to see much more detailed animations of these sketches. Further, we should also expect that they will cover topics across a spectrum of beliefs and opinions.
Especially common will be presentations on a range of social and cultural topics. Because these will be available on platforms other than the now popular youtube.com we can expect that there will be considerably greater latitude in the topical content and its adherence to "community standards", i.e. considerably relaxed oversight and censorship.
- Manipulation - Persuasive Messaging. Commercial deep fake video tools enable a skilled user to create videos that are seamless and utterly convincing. These tools allow a user to create a scripted or unscripted video. Amateur actors or non-professional stand-ins can be used to recite a prewritten script. Or a speaker can carry on extemporaneously. After a recording of the speaker is captured the facial image of another individual can be smoothly mapped onto the face of the actor. The result is stunning. Even a trained and attentive observer will find it difficult to impossible to determine that a switch has been performed. This capability means that any kind of messaging can be created for any purpose . A small team can create a message that possesses powerful messaging and inflammatory content that can motivate people to take individual or collective action outside of usual social bounds.
- Political Messaging: individuals seeking political office create and disseminate their campaign platform statements and disseminate them throughout their respective electoral districts; creating these to address local hot button issues can now be done very quickly. In the political context the facial image of a well known person, a celebrity or politician can be used to appear to be promoting a particular stance. In the following we can see the use of deep face video technology using a known image of former President Obama to promote a position. Note that the face of any other individual can be used. The target face is the one that will be available for viewing.
Detecting clever deceptions will be extraordinarily difficult to detect and falsify. Deep Fake Video can as well be used to deliver a statement or speech that they never have in the actual real world. For instance we can see how an existing image of former President Obama can be used to create a new image of President Obama saying things that he has never said. The possibility of determining if Obama actually made the statements that can be attributed to him becomes very very difficult.
Or as mentioned above, a small team can use a commercial tools such as XYZ and totally private individuals to create a deep fake video and ascribe a statement to a celebrity or politician. Again, determining if the video was real will become remarkably difficult.
Recent news reports have detailed how knowledgeable users have created voice clones of individuals. They were then able to swindle unsuspecting recipients out of thousands sometimes tens of thousands of dollars with false emergency messages using cloned voices of loved ones.
In one instance a woman was swindled out of almost ten thousand Canadian dollars as a result of an emergency call. The caller purported to be her daughter. But was in fact someone who had succeeded in acquiring a few seconds of audio from her daughters voice.
In a similar case a scammer demanded ransom money using the deception that her daughter had been kidnapped.
- Entertainment
Those who follow Dr Alan Thompson will know that he uses an avatar that he has labeled Leta. The Leta avatar is a synthetic person with remarkably lifelike features and behavior. Over the course of a "conversation" with Leta, Dr Thompson engages in discussing a range of topics of the day. He has clarified that in order to make the appearance of a dialog seem realistic and authentic he spells out that he has to resort to a number of behind the scene actions. These actions result in what looks like an ongoing real time dialog.
The Synthesia.io company is a prominent avatar provider of very realistic looking humans. The company uses advanced image synthesis to create these artificial persons. The company has also shown that lifelike expressions and gestures can be incorporated into an avatar of choice.
Looking forward just a small distance it is not unrealistic to suggest that whereas Syntheia.io is an open market provider other players will step into that market place. These new players may present themselves as open market, legitimate providers of this capability. But we should expect to see gray market as well as black market entrants. These last two types will offer synthetic personalities of any type. Therefore we should expect to see current and prominent individuals being cloned for nefarious purposes.
Accordingly it is not far fetched to imagine a situation wherein a video were to be created of a recent prominent public figure having a conversation with another figure. The other conversationalist might be portrayed as being a member of an illegal organization; this could be played out such that the prominent individual appears to be engaging in weapons trafficking's.
- Scriptwriting (see also:) Novels: a remarkable capability that CG4 has shown itself capable of is in the creation of narrative that can be used for the creation of a screen play or novel; it is capable of generating; it is capable of generating seemingly realistic characters from just a few initial prompts; these prompts can be further elaborated upon and refined to the point that a very believable character can be generated; a set of characters can be created each of which has their own motives, concerns, flaws and resources; using a set of these fictitious characters it is entirely possible to create a story line in which they each interact with each other; hence a whole screen play or even possibly a novel can be developed in record time;
- NPC: immersive role play: along similar lines CG4 is capable of being used to create artificial environments that are suitable for online immersive role playing games; these environments can possess any features or characteristics imaginable; if one were to look a short bit forward in time the industry of interactive role playing games may well experience an explosion of new possibilities;
- Synthetic Personalities: given the resources in terms of time and insight a knowledgeable user can use CG4 to create a fictitious personality; this personality can be imbued with traits, habits of thought, turns of phrase, an autobiographical sketch of arbitrary depth and detail; it can then be invoked as an interaction medium to engage with a user; these can mean engaging with an artificial personality with broad insights about the world or much more narrow but deep insights into specific knowledge domains; interacting with such a fictitious or synthetic personality might bear a powerful resemblance to training a surprisingly sophisticated dog; except that in this case the “dog” would be capable of sustaining very high levels of dialog and interaction.
- Scalable Composite CPs. When we examine the emerging directions that tool creation are going in then we should expect to see tools emerge that enable the creation of far larger ensembles of CP4, or its derivatives. These scaled up versions might be available as "off the shelf" modules that offer "plug and play" capability. This kind of interconnectivity and interoperability will mean that highly refined and very unique combinations of capabilities will emerge that will be dedicated to perform specific tasks at levels of sophistication not known today. Ilya Sutskiver has intimated that it might be possible to have an ensemble of "friends" who are the "smartest people you know" who are all working at electronic speed. They each would possess expert levels of competence and knowledge about specific domain areas that are germane to a user's goals. Current efforts with mega-personas suggest that this time has arrived. We may well be witnessing the emergence of what Marvin Minsky hypothesized in his Society of Mind book.
- Personal Relationships (Harari – 11:30). Interpersonal skills are often daunting for many people; socialization, economic, political, religious and other predispositions can condition the development of a gradually improving relationship, or conversely a worsening of it; being able to recognize, articulate and manage differences can be costly and time consuming; at worse they can result in costly and acrimonious separations; being able to head these pathways off before they pass a point of no return will be a huge step forward in facilitating the creation of positive relationships;
- Financial. Access to quality financial advisors can be very expensive; the ability to query a system with a high level of financial expertise will propagate improved financial decisions far beyond where they currently stand, i.e. affordable only by financially well to do individuals;
- Political. This might mean recognizing a local issue, creating a local community ground swell of interest then forming a political action committee to bring to a local political authority for address and resolution;
- Psychological. Existing psychological systems have already demonstrated their usefulness in cases of PTSD; going forward we can envision having a personal therapist that possesses a deep understanding of an individual person’s psychological makeup; such an advisor would be capable of helping the individual to work through issues that might be detrimental to their further pursuits or advancement;
- Support, anywhere, any time. Would we even know if the person talking on their fone using a headset is talking to an actual person on the other end? With current text to speech and speech to text we might not. Recent trials have shown that using an artificial intelligence system as a psychotherapist have shown unexpected and guardedly positive results. What happens as they become more conversant, empathetic and insightful? It might become very common to have direct access to a personal support capability at any time, wirelessly. In 2014 the USC Institute for Creative Technologies trialed a tool SimSensei. The intention was to use this tool as a proxy for interacting with individuals with PTSD. This approach used facial and gesture recognition to typify and categorize internal mental states of a patient. More recently CG4 has become an increasingly hot topic in the field of mental health.
- Professional Development. Work place realities reflect the fact that social, economic and political shifts can cause surprising and sometimes dramatic changes; these might entail off shoring, downsizing, outsourcing; therefore any individual aspiring to remain on top of their professional game will need to be alert to these shifts and able to make adjustments in changing their mix of professional skills;
- Collaborative Advice. Recent research has shown that CG4 can be configured such that it can exhibit the behavior of multiple different personalities. Recent efforts have termed this capability as mega-personas. The metaphor of a team of experts might be a suitable example of how an ensemble of CG4 instances can be structured and made available. Each persona can posses specific and highly refined expertise in various domains or various aspects of a particular domain. Communicating with this kind of system would be comparable to being able to have conversations with a range of different experts. They might be configured to communicate and interact with each other or they might be configured such that they only communicated with the end user. The recent paper called Out of One, Many: Using Language Models to Simulate Human Samples
Collaborative Problem Solving. (Zoom online meeting, July 2023), Most net-literate individuals will instantly grasp a reference to a communication tool such as Skype or Zoom. These have become so commonplace that we regularly see broadcast news interviews where a participant will be discussion a topic using either Zoom or Skype.
With the more recent versions of Skype it is now possible to hold conferences with several dozen individuals simultaneously. With the Zoom variant one is obliged to operate as if they were hosting a meeting, conference or class event. In either case it is possible for multiple participants to interact simultaneously both verbally and visually. Which on reflection means that the existing practice of gathering a number of individuals together, typically in a meeting place, venue or room has been carried over and is being used as a proxy to repeat the process though in a geographically distributed way.
Possibly less obvious is the implicit assumption that all communications, despite it being mediated electronically must function at a pace which humans now use. This is to say, using ultra low bandwidth modalities. An argument can be made that more is communicated with non-verbal clues when individuals are meeting in the same physical space. However this does not change the fact that humans are still using extremely low bandwidth communications structures.
What we do know is that information processing systems exchange information at electronic speed whether in the same room or across the planet. Therefore why would we assume that when we add the component of a knowledge intensive capability and couple it together with other knowledge intensive systems that these too would exchange information at the glacial pace that humans use.
As of this review what is stands out that we can couple these new systems together and facilitate vastly larger exchanges of information and knowledge between themselves far in excess of that of humans.
Representation Abstraction. By this we mean that there seems to be no obvious reason that we should expect to see machines communicating with each other in human language. No more so than that we expect to see a real time stock market equity price from a source such as Finance.Yahoo.com to communicate with our pc using human language. Instead they are exchanging numeric and formatting information at electronic speed.
The 1970’s movie ‘Colossus – The Forbin Project’ was based upon a novel written by DF Jones in 1966. In the story narrative upon being switched on Colossus almost immediately detected the presence of another entity comparable to itself and expressed the desire to have a communications channel to it established. Because that other entity had been created by the Soviet Union the leadership of the US tried to prevent this from happening. Ultimately they acceded to the request and allowed for a channel to be opened.
Bandwidth. In a very short period of time Colossus and Guardian had established a means of communicating with each other symbolically. Their exchanges quickly migrated to mathematical representations. Within hours their exchanges were using representations that no human had any insight or grasp of. We should expect that the exchanges between these knowledge based systems to be comparable both in volume and complexity. In short, human intervention would simply bog down the exchange of very deep and broad knowledge elements.
The FaceBook AI agents "Bob" and "Alice" were AI agents that Facebook developed several years ago. They developed a private language that it used to communicate with each other. They were programmed to negotiate the purchase and sale of various items. Bob and Alice - FaceBook technical staff discovered this they found it surprising and unnerving. This was because the agents optimized their behavior such that they created their own short hand to expresses various imperatives or interrogatives.
Autonomous agents could well develop their own shorthand or be directed to create their own shorthand as a means of facilitating efficient exchange. This remains to be seen.
By way of corroboration the results of a group of researchers at Stanford University and Google recently published a paper on how they created a version of the popular Sim World game.
They created an artificial village with twenty five “inhabitants”. Each of these independent agents possessed motives, background and history, interior monologs and were able to create new goals as well as interact with each other; the results were startling; a significant development was that the system exhibited emergent properties that the developers had not originally expected; looking forward we can expect that these kinds of artificial environments will proliferate and improve their sophistication, often with a range of unexpected emergent properties.
Of course we should expect that we can instruct these agents to interact at electronic speed instead of the snail’s pace that humans operate at. Further it is not outside of reason to expect that we can prescribe specific instructions, goals or memories to one or another of these agents such that their new goals direct the interaction of the entire ensemble of agents in one or another direction to achieve a specific outcome.
Control of these environments will operate at a very high level of abstraction, probably using a combination of voice and touch screen capability. The Cintiq line of high performance pen tablet devices points in that direction.
Schematically we might expect to see new value propositions that involve the use of multiple individual or corporations coming together to provide expertise and connectivity to a marketplace that is cognizant of the power and leverage that the new reality of deep learning offers.
The following table suggests a very simplified diagrammatic summarization of how we could see something like Zoom taken into a higher dimensional space.
Prototype Collaborative Cognition (2023).: Based upon socio-cultural modeling and analysis (socioeconomic, political, geopolitical interaction analysis using multi-agent environments); a group of researchers at Stanford University and Google recently published a paper on how they created a version of the popular Sim World game. They created an artificial village with twenty five “inhabitants”. Each of these “inhabitants” or agents possessed motives, background and history, interior monologs and were able to create new goals as well as interact with each other; the results were startling; a significant development was that the system exhibited emergent properties that the developers had not originally expected; looking forward we can expect that these kinds of artificial environments will proliferate and improve their sophistication, often with a range of unexpected emergent properties;
We should expect to see an intelligent interface control protocol that resembles those found with pen tablet or otherwise touch screen capabilities. A baseline approach that might suggest a way forward can be seen with the Cintiq line of pen tablet devices.
Schematically we might expect to see new value propositions that involve the use of multiple individual or corporations coming together to provide expertise and connectivity to a marketplace that is cognizant of the power and leverage that the new reality of deep learning offers.
By way of schematic presentation we show a table (below) in which a CG4 user is making use of both a supporting instance of CG4 and a link to IBM Studio. It consists of three cognitive elements (CE's).
| CG4.00 | ||
| CG4.01 | ||
|---|---|---|
| IBM.01 | ||
2023.07.21: need to review paragraphs below, get them back in coherent order;
We can envision a nascent environment wherein multiple autonomous agents might be controlled by a specific individual. That individual might bring their ensemble of experts (IBM05 and IBM07) together with a number of other individuals. These individuals might form the new basic collaborative cognitive service. A client might contract with a representative for this cognitive service for access with specified durations.
The following schematic representation of a collaborative cognitive environment suggests a single controller, identified as CG4.03 who has established communications with two different instances of IBM Watson, IBM.05 and IBM.07. In this situation the controller might be interacting with the two WATSON instances asynchronously. The communications channels would be such that the controller, via CG4.03 would issue prompts to IBM.05. On processing, IBM.05 would respond back to CG4.03 directly.
At the same time, CONTROLLER CG4.03 an be issuing instructions to IBM.07. The results provided by WATSON.07 would be returned to a separate instance of CG4 that the same individual was controlling. Thereby enabling asynchronous but parallel cognitive processing.
The following table suggests a very simplified diagrammatic summarization of how we could see something like Zoom taken into a higher dimensional space.
We envision a nascent environment wherein several individual can offer to provide their specific expertise for sale. They might each have their own account with a cognitive provider (OpenAI, DeepLearning, Gemini or some other vendor).
They might individually or as a group elect to have an intermediary act on their behalf to work with a client and disambiguate specific client requests. This intermediary might be a regular team member that the specific experts are comfortable working with.
In this first schematically presented case the intermediary might be CG4.00. This might be an individual who has worked with the experts. In the one case one is identified as CG4.01. The other is labeled as WATSON.01.
For whatever reasons this team may be the group of choice for specific purposes and tasks.
| CG4.00 | ||
| CG4.01 | ||
|---|---|---|
| IBM.01 | ||
In a different setting we could see a configuration wherein there can be a single instance of CG4 communicating with two different instances of WATSON. These two different instances of WATSON might differ from each other in terms of the contents of their respective knowledge bases.
To view this more concretely a financial analyst might be studying the bull position for a particular equity. At the same the the analyst might also want to evaluate a bear position for that same equity. In other words, perform a "devil's advocate" set of positions that can be used to offer insight on how to assess the riskiness of a particular choice of actions.
In another setting we can envision a small team consisting of four individuals. A team leader might make use of two cognitive provider accounts. In this case that individual might use one that is fine tuned for one set of purposes and the other could be fine tuned for domain specific disambiguation purposes.
Three other team members might each provide specific domain insight such as that relating to financial analysis, geopolitics and a third specializing in the impact of interest rate hikes on specific industrial sectors.
| CG4.01 | ||
| CG4.02 | ||
|---|---|---|
| IBM.01 | ||
| IBM.02 | ||
| IBM.03 | ||
What has recently come to the fore (July 2023) is the fact that CG4 can be configured to interact with separate instances of itself. These are called agents. Researchers at Stanford University and Google worked together to develop a means whereby CG4 could initiate multiple instances of itself to function asynchronously and independently of each other. They were configured such that they could interact and communicate with each other. Each agent was provided with goals and memory. They were able to interrogate episodic memories of events and interactions that they had during a session. The result was that they demonstrated surprising emergent behavior. This became interesting and engaging for the researchers because the emergent behavior began to exhibit group behavior with unexpected outcomes that had not been originally stipulated in the initial programming.
Recently, informed observers have demonstrated how CG4 has been configured such that it is able to communicate with less sophisticated instances of itself. In a recent presentation an observer described how ChatGPT4 was able to dispatch an instance of ChatGPT3.5 to perform a specialized sub task asynchronously. Then incorporate the result that the ChatGPT3.5 instance provided on completion of the sub task.
Using this logic it stands to reason that it might be possible to have a specialist operator with expertise in a particular domain area. That individual could instruct an instance of CG4 to dispatch one or more instances of ChatGPT3.5 to perform one or more sub tasks on its behalf.
Extending this approach would not be farfetched were there to be several domain specialists who functioned as a team concurrently. Each might have their own CG4 account. A client might present them with a problem for solution. The specific problem could require the knowledge and insight of several specialists. In the following schematic table we postulate a working session wherein several individual controllers are "driving" their specific CG4 instance. In one case a controller is "driving" their ensemble using an IBM instance.
As necessary three of the instances (CG4.30, CG4.40 and IBM.01) have their instances configured to dispatch CG3.5 instances to perform specialized processing.
In the case of CG4.30 and CG4.40 a CG3.5 subtask is dispatched (CG35.31 and CG35.41). Each of these are able to dispatch a sub tasks of their own. For example in the case of CG4.40 the CG35.41 sub tasks is dispatched but it requires further support from CG4.42 and CG4.43. These would all terminate after they had provided their results "back up the chain".
Overall cognitive state at beginning of session. Note that communications between each instance can be asynchronous. Further, constraints on message size and format is assumed to be relaxed.
| P 1 | P 2 | P 3 | P 4 |
|---|---|---|---|
| CG4.10 | CG4.11 | IBM.12 | IBM.13 |
| CG4.20 | CG4.21 | IBM.22 | IBM.23 |
| CG4.30 | * | * | * |
| CG4.40 | * | * | * |
| IBM.01 | CG4.01 | * | * |
Overall cognitive session during problem solving (snapshot).
| P 1 | P 2 | P 3 | P 4 |
|---|---|---|---|
| CG4.10 | CG4.11 | IBM.12 | IBM.13 |
| CG4.20 | CG4.21 | IBM.22 | IBM.23 |
| CG4.30 | CG35.31 | CG4.32 | CG4.33 |
| CG4.40 | CG35.41 | CG4.42 | CG4.43 |
| IBM.01 | CG4.01 | CG35.012 | CG35.013 |
Problem solving is very well known to be a highly dynamic and volatile sequence of events. Therefore we would expect that in the case of sub tasks, their associated cognitive processes might "blink" into existence and abruptly "blink" out of existence as they finished performing their work.
Overall cognitive state at end of session.
| P 1 | P 2 | P 3 | P 4 |
|---|---|---|---|
| CG4.10 | CG4.11 | IBM.12 | IBM.13 |
| CG4.20 | CG4.21 | IBM.22 | IBM.23 |
| CG4.30 | * | * | * |
| CG4.40 | * | * | * |
| IBM.01 | CG4.01 | * | * |
Note that the CG3.5 instances are not counted in the description above because they might exist for only as long as they need to complete their specific sub task. Therefore, CG35.31, CG35.41, CG35.012 and CG35.013 might be absent at the beginning of a working session and then again at the end of a working session since they can have completed their specific sub task.
Controlling a cognitive tool such as CG4 will evolve to involve controlling multi-step actions. These will be very much like invoking a function or routine in traditional programming. An interface capability to control the cognitive ensemble configuration and "driving" process will need to be intuitively obvious. What should become directly evident is that having this kind of high level cognitive capability available represents a step into a higher dimension of capability and value.
We can envision teams of individuals working collaboratively together producing results in real time in response to rapidly shifting public perceptions; they might be co-located or geographically dispersed; in the example shown above they might be using high performance pointing devices to control sophisticated Deep Mind processing;
Development Path. Looking forward we will very likely see ensembles of agents much like the society that the Google and Stanford team created resulted in a small village with twenty five “inhabitants”. Each of these “inhabitants” were GPT based agents. Each agent possessed motives, background and history, interior monologs. A team might act as the high level interface to a very large ensemble of CP's; these could range up into the hundreds or thousands.
They were able to pursue goals either individually or collectively. They are able to create new episodic memories which can be used to compare the results of recent events to existing goals. In the process they were able to self-improve their performance. As the model played itself forward some surprising and starling results became evident. What happened was that the system gradually began to exhibit emergent properties that the developers had not originally expected. This suggests that arriving at a desired solution might involve navigating a multidimensional space with a variety of peaks and valleys. In short, the more interesting problems will not have a direct linear path to their identification. If we look forward a bit then we should expect that these kinds of cognitive environments will proliferate and improve their sophistication, often with a range of unexpected emergent properties. Further, we should expect to see heretofore unexpected emergent behavior.
Society of Mind. A recent effort by teams from Google and Stanford University demonstrated how socio-cultural modeling and analysis was described in a recently published a paper. Their analysis was very similar in its operation to the popular PC Sim World game. (Note: Society of Mind was a book written by Professor Marvin Minsky (MIT) which explored how the brain’s neurons organized themselves into collections to perform specific tasks. In short, he viewed the brain as a society of minds). What these recent Stanford and Google researchers have done is to have created a “micro” version of what Minsky was proposing. In this case however the agents represent elements of a society.
A logical next step will be the enablement of each individual to have their own CG4 (CG5?) instance available and accessible to all participants such that these instances can perform real time exchanges. When this happens then we should expect to see a proliferation and explosion of what might be described as a "composite mind". In this instance we might see situations where interacting CG4 instances were only able to communicate with each other during a live session. In other instances these might be taking place asynchronously between participants. Obviously this means that the same Metcalf power law that applies to networks will apply to these collections of "minds". The greater the number of nodes on a network the more valuable it becomes.
This seems to be a logical and plausible next step in the further refinement and usage of tools such as CG4 will be collaborative environments. These kinds of collaborations can be envisioned as consisting multiple simultaneous users. Operationally this form of collaboration would bear a strong resemblance to a WEBEX or Zoom call.
Participants might participate online in real time. They would wire together their various instantiations of CG4 together into a network. This network could utilize any of the standard forms of connectivity (B*Tree, mesh, ring, bus, star); each agent might act either under direction of its owner or it can act autonomously. The result would be a composite entity. The would result in a new reality wherein the whole would be greater than the sum of its parts. CG4 can establish a linkage to the IBM Watson system via the IBM Watson API. IBM Watson API.
This stepping forward to computationally mediated communication introduces novel possibilities. For instance one can envision an model wherein all participants use the same CG4, in another instance the processing elements might be heterogeneous. Currently the other major knowledge based artificial intelligence system that can be directly access via its API is the IBM Watson Studio.
In other settings one might see the use of IBM Watson or some comparable variant; judging from the pace of progress we deem this to be a very high probability, high value/payoff approach; because of the flexibility of interconnectivity and interoperability this model can scale to arbitrary size;
This is just an example, and the specific methods you use will depend on which part of the Watson API you're interfacing with. The Watson API provides many different services, including natural language understanding, speech-to-text, text-to-speech, visual recognition, and more.
Of course these assemblages can be scaled as appropriate and the problem scope requires. Further one can envision a marketplace individual and organizations that specialize in specific knowledge domains. These might might be available on an ad hoc or persistent basis depending upon the need and the economics.
A review of the network topology diagram (above) suggests that agents can be interconnected together to gain the maximum leverage for their respective specialization. In one configuration there might be a moderator whose primary task would be to orchestrate and sequence how results are prioritized. This might bear resemblance to a STAR network topology. In this case the moderator would receive all output from the supporting agents. From there prioritize each output and forward it to a client.
In another configuration we can envision a situation wherein the connectivity resembles what is called a BUS architecture. In this configuration messages are sent out as they are received. If there is one or more exchanges already in progress then a random (if small) "back off" interval is executed before a retry happens. Otherwise messages would be distributed to all agents whenever they can be sent.
Working from the work done by the Google and Stanford team that created the Agent Sim environment we can imagine that a serious working system might extend beyond a 'plan/reflect' loop. Other factors might be incorporated beyond this simplified version.
Political Action.
Sentiment Analysis. The British company Cambridge Analytica became well known through its ability to analyze voter sentiment across a broad range of topic and hot button issues; it excelled at creating highly specific messaging to remarkably small target groups that led to decisions to vote or not vote on specific issues;
Preemptive Campaigns. Existing analysis tools such as sentiment analysis will become increasingly sophisticated; as the do we should expect that they will be applied to public figures, especially legislators and others in positions of influence; these insights might be based upon public actions; in the case of politicians voting records, position papers and constituency analysis will be at the forefront of study;
Subversion.
Personal Compromise. Access to detailed information about information about individuals of interest such as those with national security or defense related clearances will be favorite targets of malicious actors; the recent attack on the Office of Personnel Management is a foretaste of what is to come; by gaining access to information about individuals with highly sensitive clearances a foreign actor can position themselves to compromise, threaten or otherwise coerce specific individuals with clearances or people who are directly or indirectly related or associated with them;
Extortion. The Office of Personnel Management of the US Government was hacked by PRC hackers. The result was the capture of millions of profiles of US citizens with security clearances. Possession of the details of these individuals puts them at considerable risk. Risk factors include: knowing where they work and what programs they have access to, data on relatives, co-workers, detailed identification information suitable for creating false credentials.
Counter Intelligence specialists have over years identified four major reasons that motivate a person in a trusted position to betray their trust. These four reasons are summarized as MICE: M: Money I: Ideology C: Compromise E: Ego
Foreign agencies are constantly on the lookout for targets of opportunity that can be be willing or unwittingly compromised. Once they have been identified it is then a matter of identifying a pathway to an encounter that would enable capture.
One of the biggest data breaches occurred in 2015. The Office of Personnel Management had an unknown amount of extremely sensitive information about all government employees with a security clearance. This breach can have consequences lasting for years or longer. In the diagram below a dense network of connection is evident. In most cases a given individual will have no idea of the other people who are in that network of connections. They may never encounter any of them or know any of them. The degrees of separation specify how many introductions are required in order to bring one individual in the network into direct or close if indirect contact with a target. Typically this will be five or often less.
The current reality of massive online databases detailing stunningly detailed information on nearly everyone alive within a nation means that the ability to capture this data and use it against the target nation is very great. With a deep learning system the risks eclipse those that have existed in the past. This obtains from the fact that it is now possible to create very detailed plans of action that would enable gaining access to a desired target individual. By using information captured from one or more of the major credit agencies then identifying and maneuvering a compromised individual becomes orders of magnitude easier than in the past.
Possession of this type of information can enable an adversary to be highly selective in targeting prospective individual who might be susceptible to compromise, blackmail or being suborned otherwise. An attack vector could be via a direct path or could involve threatening or intimidating a family member. The possibilities are endless.
A cursory review of a network connectivity graph should make clear that the numbers of connections between people can become surprisingly large. Where an individual might themselves know perhaps only a few people, one or more of those individuals that they know might in fact know a surprising number of people. The result is the prospect of surprisingly dense social network.
In the case of an adversary the map lays out very plainly who might be a target and how to get at that target. Considerable attention has gone into the advent of 5G networking. In 5G networking the numbers of connections per square mile or square kilometer is orders of magnitude higher than that of prior wireless networking connectivity. On the order of 2.5 million connections in a square mile. Or 1 million connections per square kilometer.
What is rarely discussed is the relative proportion of voice connections vs. machine connections within that same boundary area. In the case of 5G these devices can be automobiles, elevators, escalators, microwave devices, cell tower repeater equipment, video cameras, traffic lights and many other kinds of electronicky actuated equipment. An adversary capable of infiltrating a 5G communications system can identify specific targets for various kinds of attack vectors. For instance a situation can be imagined where a particular person is a target. They may find themselves stranded at a non functioning traffic light. On activating the traffic light back to normal operation cause it to inappropriately respond to the cross traffic. The upshot could be a serious vehicle collision with the intended target being the one being impacted.
In another scenario they might be on an elevator in a tall building. Seemingly, spontaneously the elevator might halt between floors for many minutes or much longer. The upshot being that the target individual could miss a flight. Add in that wireless telephone service could also be disabled for that immediate locus. Effectively putting that person out of contact.
Molecular Modeling.
Tool or Weapon. A committed agency or group can use a tools such as CG4 to refine molecular models to accomplish specific purposes. For instance the developing field of polymer dendrimer molecules enable the possibility of creating molecular structures with heretofore unimagined capabilities. By way of summary, a dendrimer molecule is a specific type of molecule that consists of a series of layers. Structurally they loosely resemble an onion.
Dendrimer Molecules. Relatively recent developments in molecular design have brought to light molecules that can be layered. Dendrimer molecules can be used for a variety of purposes such as the creation of substances with very novel features. Surfactants can be constructed that offer hydrophobic behavior. Other dendrimer structures can be used for drug delivery. A keen observer will note that this technology can be used for both ethical, constructive purposes as well as non-ethical purposes. The range of potential uses is sufficiently broad that a catalog of possibilities would be very difficult to articulate.
Dendrimer molecules can be fabricated such that they resemble a layered object. In the abstract a dendrimer molecule bears some resemblance to an onion. Multiple layers can be generated such that a payload molecule can be embedded within the dendrimer molecule. A highly specific and concentrated molecular substance can be embedded between layers. The dendrimer molecule is therefore an excellent pharmaceutical transport mechanism. The range of possible uses is continuing to grow as new uses are identified for this developing technology
Because there can be many layers a dendrimer molecule can be assembled such that a range of different molecular payloads can be embedded and delivered; depending upon the requirements of the application these layers can be tuned to dissolve at predetermined rates and under known environmental conditions. These layers or shells can be used to embed a "payload" of specific molecules. The shell or layer can be designed such that it will erode or dissolve in its intended environment after a predefined period of time.
This means that any imaginable combination of substances can be imbedded within the layers of a dendrimer molecule. These embedded substances can be either beneficial pharmaceuticals or they can be weaponized substances that can have powerful and profound physiological and or psychological effects.
Notice in the following diagram that one can see the progressive stages involved in constructing a dendrimer molecule; by stage three we can see how payload voids have become available; it then becomes possible to mount highly refined and specific molecules into these voids; depending upon the embedding layers we can determine how, when and under what conditions the payload will be released; by generation 4 one can recognize that a prior payload has voids available for other molecules;
As of July 2023 thirteen generation dendrimer molecules have been successfully fabricated.
Below we can see a more symbolic representation of how many different payload molecules can be imbedded within a dendrimer molecule; the result is that there is a very large range of possibilities;
Because just about any imaginable combination of molecular payloads can be carried by these delivery systems the possibilities are endless; and this likewise means that this means that this will prove to be a double edge sword; what must be clear from this development that a CG4 type tool can be put to dual use purposes. Remarkable results have been being published in the area of senolytic research. Teams at MIT, Harvard and X-Biosciences have recently been reporting breakthrough developments in the area of safe and effective senolytic compounds.
The are molecular compounds with properties that can act directly on senescent cells in the body. Senescent cells are cells that have stopped dividing and are now in a "zombie" state. The body fails to remove these cells that become both an obstruction as well as a source of inflammation. Over time they accumulate in bodily tissues and organs. The result is that as more and more of these non-functioning cells accumulate they interfere with the normal and effective functioning our various metabolic pathways.
A method of inducing the body to remove these inactive cells would go a great distance in arresting and possibly reversing what is now called "aging". Current research is actively being pursued to test and prove the efficacy of the new molecular compounds so as to identify effective treatment regimes.
Increasingly more and more researchers are applying deep learning models to their efforts. Recently researchers at the University of Edinburgh and the Spanish National Research Council IBBTEC-CSIC in Santander, Spain used a deep learning system to identify candidate senolytic compounds. They provided it with over four thousand compounds found in the DrugAge Database as training data. Within five minutes it identified three promising molecules. One of which, oleandrin proved to be remarkably effective with its senolytic properties.
In related news, Integrated Biosciences, the Broad Institute (MIT) and Harvard used a deep learning system to screen 800000 chemical compounds.
Novel Psycho Actives. Dendrimer technology can be used to fabricate combinations of pharmaceutical substances for highly specific and focused effects. Were an agency or group to decide to use a tools such as CG4 to design a novel molecular structure then it does no seem to be out of the realm of reality that the most sophisticated combinations of molecular structures could be designed and delivered to a target; because these are at molecular scale they could be made to be effectively undetectable; they could be made to react to various environmental conditions or activate based upon a time release scheme; further they can be made to use the same payloads but have these payloads released at varying intervals; the possibilities are limitless;
Targeted Bioweapons. The ability to synthesize and model new molecular structures will be hastened with tools such as CG4; the rival company Deep Mind recently supported the effort to arrive at a SARS COVID-19 vaccine; the company used its Deep Fold 2 system to screen millions of possible vaccine molecular structures; the result was that it arrived at a small set of viable candidate molecular structures in a matter of days; equally possible would be molecular structures that were capable of causing debilitating physiological or psychological functioning;
Carbon Nanotubes. These are novel molecules with extremely regular lattice-like structures. They can be used to fabricate materials with novel properties. These properties can be targeted to result in materials of extremely high tensile strength, filtering capabilities and innumerable other specific applications.
Inorganic (materials, pharmaceuticals such as dendrimer, mono-filament molecules) such as: Room Temperature Superconducting Materials. Such a development would revolutionize societies in ways that cannot be fully characterized; another usage of such a capability might be in the fabrication of power storage capabilities; these forms of molecular combinations could result in storage batteries with power densities hundreds or thousands of times beyond those currently available; a battery the size of a loaf of bread might be capable of storing sufficient power to operate a standard home with all of its devices operating for days, weeks or longer;
Extremely High Tensile Strength Materials. These might be derivatives of carbon nanotube material; but with much higher tensile strength; fibers made out of such material can be used as a saw blade; strands and weaves of such material could be used as a space elevator material; other uses might be in the use of nearly impervious shields such as bullet proof vests if woven into a fabric-like material and covered such that it did not endanger the wearer;
Organic (Biological) Modeling Capabilities. This can include a variety of structures(proteins, enzymes, hormones virus, bacteria, prions) The identification of molecular structures that enable the interdicting of metabolic failure can be envisaged. This could mean that new tools can emerge that go beyond the already remarkable CRISPR-CAS9 model and its derivatives. One can envision the creation of variants of molecular substances that mimic the hemoglobin molecule found in certain reptiles such as alligators or whales. These animals routinely demonstrate the ability to remain submerged for many minutes on end without resorting to returning to the surface to breathe.
Combined Novel Molecular Modeling Capabilities. New multipurpose materials(substances, pharmaceuticals). These materials may be the result of combining organic and inorganic molecular structures to arrive at a result with heretofore novel and unexpected properties and capabilities;
In recent weeks an awareness has begun to rapidly crystalize an awareness of the possibility of dual use molecular design and synthesis. The recent reporting that focused on Combinations Pharmaceuticals is a case in point. In this case the company fabricated its own deep learning tool. Its primary focus and cause for existence was and is for the discovery of viable, safe and useful pharmaceutical drugs.
Their discovery that deep learning neural networks could be used to facilitate search prompted management to opt for a targeted system capable of learning about how molecular compounds are structured. After a period of training their MegaSym system was dispatched to search for promising drug candidates for various purposes. On a whim their chief researcher Dr Urbani decided to flip the value associated with toxicity from a zero to a minus one. The result was that within six hours the deep learning system had generated a list of approximately 40000 chemical substances. In many cases the results were far more lethal and toxic than VX. A bit more on this momentarily.
Novel Protein Design. Recent developments in using deep learning systems has been the emergence of protein designs that are 'made to order'. These are protein structures whose properties a protein designer can specify. Within minutes the design software, known as RFdiffusion is able to offer molecular structures for review. It is now available as an open source software tool.
It is not far fetched to consider that this tool can be used for purposes that might have been considered science fiction just a few years ago. A case in point might be using a variant of this RFDiffusion tool to devise a variation on the human hemoglobin molecule such that it has substantially greater oxygen retention capacity. Mammals such as dolphins and whales might reveal ways in which their hemoglobin might be adapted for human purposes.
A great deal of progress has been recorded in the area of the field of genomic manipulation as a result of the development and refinement of what are called CRISPR-CAS9 editing tools. These are molecular level tools that are capable of performing very precise editing of the DNA molecule. CRISPR-CAS9 and its derivatives such as CRISPR-CAS13 allow for the snipping out of highly specific sequences of lengths of the DNA molecule and replacement with a desired length. This means that hereditary problems such as Tay-Sachs, Cystic fibrosis or cycle cell anemia can now be treated.
In other uses it is now possible to genetically splice traits from one species into the DNA of another. In recent years progress has shown that the enzyme known as luciferase can be spliced from firefly DNA into the DNA segment responsible for skin coloration. The result is that one can now have animals that glow in the dark.
Synthetic Molecule Design. (MegaSyn VX Ekins Urbina North Carolina) Recent work at the University of North Carolina in collaboration with a private firm known as Collaborations Pharmaceuticals. resulted in a list of approximately 40000 chemical structures with known toxic to extremely toxic properties.
The list of toxic chemical substances was generated in a six hour period using an deep learning artificial intelligence system operated by staff at Collaborations Pharmaceuticals. Researchers discovered that many of the chemicals discovered were as dangerous or far more dangerous than the VX nerve agent which is odorless and tasteless and kill within minutes on contact. On reviewing their results scientists recognized the seriousness and risks associated with having a tool such as MegaSyn available. Their conclusion was that the dangers posed by this new technology were so completely off of known charts that new measures of risk and danger are requisite.
The fallout of these results has been far reaching. The researchers were invited to the White House to describe their findings and explain the risks associated. In sum because of the lethality of the chemical compounds that MegaSym discovered and the ready availability strongly suggests that a chemical attack using a bioweapon attack using a variant of VX is extreme and present.
The chief researcher at Collaborations Pharmaceuticals, Dr. Urbina had not expected that MegaSyn their deep learning tool would produce the wide range of molecular structures on such an out of date processor in such a short time.
Novel Targeted Pharmaceutical Enhancement Design. In the movie 2011 movie Limitless a wannabe author encounters an acquaintance of his while walking through Manhattan. The acquaintance passes him a small packet of tablets and suggests how they might help. It turns out that when used properly they provide the user with perfect recall. The effect that the nootropic is almost immediate. An individual who has ingested a small dosage is able to harness their ability to control both short and long term recall far beyond what is currently possible. Looking forward researchers may identify a means whereby the synthesis of selective activators as the fictional NZT-48 might become available.
Societally Disruptive Memory Enhancement. If we look forward a short distance we believe that there will be an emergence of gray market products and services that will restructure the world view of most Western societies.
These kinds of developments have been well known in prior eras. During the era known as Prohibition in the US in the 1920's and 1930's alcohol was prohibited from sale. The result was that alcohol black markets emerged. That this was so derived simply because there was an ongoing and persistent demand. So, where there was a demand, enterprising individuals found ways to either produce alcoholic based drinks or to smuggle it into the US. The result was that there was a huge market for black market alcohol and establishments where it could be bought and consumed.
This fact simply reflected a basic truth of human nature. There should be no confusion as to whether or not human nature has changed in the past hundred years. The facts speak plainly that it has no. Proof can be seen with the long awaited decriminalization of cannabis. After several years of legalization in a few states many other states have followed suite and legalized cannabis. By and large the horror stories that the nay-sayers were claiming would happen have not materialized. That events have taken this path sets the stage for the next surge forward. By this we interpret how events have played out to suggest that they will continue to play out going forward, if albeit at a somewhat more brisk pace.
What we expect to see will be a continuation of the process wherein such psycho-actives as LSD and psilocybin have found footholds in research facilities with accreditation to perform legitimate, controlled research into the effects of these substances.
Our expectation is that a range of other psycho-actives will gain traction and acceptance. However they may find themselves relegate to the gray market for some time as societies at large become more comfortable with their presence in everyday affairs and how they impact ordinarily daily commerce.
Their emergence will be facilitated by three complementary elements: bitcoin and bitcoin escrow services, small chemistry suppliers and a means of demonstrating availability and reliability of the delivered product.
It would operate along the following lines:
- BitCoin Account. A prospective client or customer would gain anonymity by establishing a BitCoin account.
- BitCoin Escrow Account. Verification of a transaction will require the services of a neutral but reputable third party.
- Precursor Supplier. The supplier would need to be able to post notice of the range of available choices.
- Anonymous Logistics. Receipt of the semi-finished product would be expedited by having an anonymous logistic point. The American logistics company named United Parcel Service (UPS) or an enterprise providing similar capabilities would suffice. It is not unusual to be able to find a UPS store. A service of these facilities are the equivalent of numbered post office boxes. Once an order has been fulfilled and delivered the customer can be notified that it is ready for pickup and the supplier can be paid thus completing the transaction. In the range of actions anonymity is maintained.
- Customer Purchase Order (CPS). A purchaser would select the specific end result molecular structure. This would be sent as an encrypted request to a known, reliable and reputable precursor pharmaceutical provider.
- Chemistry Precursor Supplier (CPS). The pharmaceutical synthesist would accept the request, acknowledge its receipt and issue a detailed invoice. This invoice would specify the precursor elements and the relative dosages and steps needed to produce the finished product.
- Bitcoin Account (BA). Each party would use Bitcoin as a means of payment. In order to proceed with the delivery the supplier would query a BES to verify that payment had been made.
- Chemistry Precursor Validator (CPV). This is an independent third party selected by the Customer. The role of this party would be to validate the reputation of the CPS for any questionable activities or irregularities. The CPS would have delivered to the CPV very small quantities to test and verify that they were what they were claimed to be.
- Bitcoin Escrow Service (BES). After payment had been made and the product precursor elements assembled, these would be presented to a second BES. This second CPV actor would then signal to the Customer that the shipment was what it was claimed to be. At this point the BES would authorize payment release to the CPS and shipment to the Customer.
- Anonymous Logistics After the elements had been shipped then an AL facility would receive them. On receipt the AL would be able to notify the box holder of the arrival of a shipment to be collected. The anonymous box holder would then collect the items and signal to the supplier that receipt had been completed. Thus closing the transaction.
Modifications and adjustments to this process might be called for but they would set the stage for effectively breaking the monopoly that the large pharmaceutical companies have on almost all ingestibles.
That this will probably develop is supported by the fact that the underpinning mechanism required to facilitate this development are already in place. The basic elements required to bring this development forward will require an approach used by high-tech micro-electronic fabrication enterprises. Advances in micro-electronic components moved forward to face market demands of scale. One approach to meet this demand, despite a wide variety of highly specific demands was to take the approach of creating semi-finished micro-electronic components.
These components used what is called Field Programmable Gate Arrays (FPGA's). These devices with a large array of just a few types of chips embedded on them. They could have arrays of processors, processors and memory chips or these as well as other devices such as analog-to-digital or digital-to analog (A2D and D2A) chips as well. A customer would specify the first pass of fabrication elements, i.e. all processors, or all memory or combinations of each. The fabrication facility would then send these to the customer. The customer would then disable those elements that were not needed and only allow the desired ones to remain connected to each other. This had the effect of reducing costs considerably.
A similar approach can be envisioned in the zone of synthetic psycho-active pharmaceuticals. In this case a customer would specify the types of elements to be delivered and in what dosages. A supplier would then provide these elements to the customer. For purposes of verification commonly available test components would be recommended from third party suppliers. These could then be used to verify that the purity and dosages requested had in fact been delivered. It would then be up to the customer to follow the final step of assembly of all of the elements to make the desired end product.
Currently there might be reasons why a gray market approach may emerge first. This is because it would involve bypassing the established enterprises and government regulatory agencies. What is so well known and established is that the major pharmaceutical companies have shown themselves to be some of the most generous lobbyists in almost all of the major Western nations. We should expect that any activity that bypasses their ability to control and therefore derive profit from will be vehemently attacked. Therefore this necessitates the third element.
Advances in the study of neuroanatomical, neurophysiological and signaling has revealed a considerable insight into how the human brain processes and stores experiences from the real world into long term memories that can be retrieved at later times.
Given the far broader and deeper body of knowledge now in our possession it is reasonable to expect that we shall see pharmaceuticals whose role will be to facilitate and accelerate the creation and retention of experiences into readily accessible long term memories. Refinements will likely also bring forward the ability to selectively focus on specific areas and topics of interests. This could mean enhancing retention of visual scenes, spans of audio information or other forms of sensory information.
Initially availability of these new classes of enhancers might only be accessible via gray markets. These might require the use of bitcoin exchanges via bitcoin escrow accounts. That this may be the pathway of last resort is corroborated by the intense pressure imposed upon various congressional committees by lobbyists for pharmaceutical concerns whose interests are to position themselves as the sole source availability of any new capability. And as such lock in a monopoly position on access to anything that might offer novel skills, competencies or capabilities.
Delivery mechanisms have become available that allow for very precise delivery of highly specific dosages and amounts of psycho-active molecules. We therefore expect that the ability to selectively enhance long term memory may be just around the corner. At such time that this becomes available then we may very well be witnessing an evolutionary bifurcation of individual who have enhanced themselves separating themselves from those who refuse to do so.
The reality of functional MRI (fMRI) capability enables researchers to focus on specific neurological pathways that enable the tracking of cortical activation processes. This suggests that in principle it should be possible to identify those pathways that facilitate short and long term recall for the purpose of optimizing extremely detailed retrieval of newly learned material or content.
Eptification. The 1968 novel Stand On Zanzibar by John Brunner broached the possibility of facilitating highly specific and targeted long and short term recall using pharmaceutical means. In the novel a character named Donald Hogan is a PhD in biology. He has been on military reserve status for some number of years. He suddenly discovers that he has been activated and is given instruction to report to a nearby military facility. The location is innocuous but is highly secure. While there he is subjected to a process known as eptification; He is trained in a variety of subjects one of which is extremely lethal hand to hand combat; his training time is surprisingly brief; however on completion he discovers that he is able to recall things that he has written with amazing clarity. Modern day techniques comparable to those used by the MegaSyn system could well sketch out a pathway to the synthesis of something along the lines of NZT-48.
Social Engineering. Our perception is that unexpected and novel social developments and processes can be set in motion and managed over time. A catchall heading for these kinds of endeavors might be the category of "social engineering" for lack of a better way to identify a catch-all. Social engineering might result in emitting messages within a social sphere with the intent of motivating and activating various groups or collections of people; in this case the individuals themselves might or might not even realize that they are being manipulated.
A CG4 category tool can be used to create models of social processes; these processes can then be characterized in terms of how various groups respond to select social messages and signals.
For some social groups there are "hot button" issues that will motivate reactions ranging from peaceful demonstrations to violent protest reactions. The more finely tuned the model the greater control can that can be exerted to induce or provoke actions, reactions or interactions. In a broader context the same ability to understand how various processes advance means that industry models can be defined, articulated, modeled and studied for heretofore unsuspected linkages and sensitivities.
Invasive Species Mitigation. This might be a problem focus in cases where an uncompromising invasive species arrives seemingly out of nowhere. Its behavior is such that it requires resources as well as accommodation on the part of the new environment that it has lodged itself into. Due to its nature and character it has proven itself to be a subtle and relatively silent pest that consumes resources and crowds out the native species.
An example of this kind of situation can be seen in the Great Lakes of North America where the Asian Carp has invaded several of the waterways. They have proven to be a voracious predator and have crowded out the other native species. In order to mitigate their presence and associated risks conservation teams have had to resort to concerted efforts to halt their advance. Some approaches have involved dropping netting across waterways. Another approach has been to use electric shock fences to turn them back.
Secret Life of Plants. Recent botanical research has revealed that stands of trees form incredibly dense communications networks through their root systems. They use these root systems to exchange nutrients and messages. They have revealed themselves to be surprisingly robust in exchanging environmental messaging as well. In the event of an invasion attempt by a predatory or parasitic species they are able to signal each other to release toxins as a means to ward off these forms of attacks.
A lesson learned in trying to deal with this problem has been that they exhibit peculiar habits such as becoming very evident and active at certain times of day. Champions for their presence have shown that by emitting a certain pitch at these times of day will cause them to congregate in certain parts of a waterway. This congregation behavior can cause interruptions in the regular flow of events. In some cases these interruptions are mild and can be ignored. In other cases when serious fishery activities are at hand these can be very disruptive. An approach is recommended that would enable minimizing and ultimately removing this burdensome and irritating presence.
Industry Models. Targeted Industry Segment Analysis – identification of bottlenecks, weak links, possible disruption points.
Using CG4 it becomes possible to model a business process in arbitrary detail. This suggests that it is possible to create models of very fine granular detail. With the appropriate control mechanisms one can study the effects of internal or external events. Such as tool would enable deep understanding about the factors that adversely or positively impact that particular process. Such a capability can be disruptive depending upon how such insight is put to use.
Exploratory Analysis. Existing modeling tools have reached a level of sophistication that major government organizations, universities and think tanks have incorporated these kinds of tools into their bag of tricks. One can envision using a powerful tool such as CG4 to model the processes of a major geopolitical development. Recent news reports (as of June 2023) offer strong indications that the US and the PRC may be heading toward some form of confrontation in the South China Sea littoral. In at one instance a major think tank known as CSIS reported their results of an exploration of events involving a PRC invasion of the island of Taiwan.
According to various reports the results varied from just tolerable to remarkably bad. A tool such as CG4 can clearly be used to model in arbitrary detail the processes that involve multiple agents, a variety of resources and any number of uncertainties, potential bottle necks and other factors that can predispose events to progress in one direction rather than another.
Process Modeling: Social, Economic, Political, Geopolitical: selectively focus on global areas of interest; the objective being the creation of tools that enable the operator to “drive” a line of analysis or discourse forward based upon real world limitations, resources, historical realities and current political imperatives; an extension to Caspian Report
Modeling commercial or industrial processes can be facilitated by bringing together individuals or sources that possess expertise or data and or knowledge about various aspects of how the target process functions. This means that actual real world processes can be modeled and driven in ways that the actual process and its elements could not. This means that any configuration of loading or overloading can be modeled as a means to stress test the robustness and resilience of the process to withstand unexpected loading. We note that this loading can take the form of being intentionally loaded by those responsible for its functioning or by those whose intent is to disable or destroy it such as an adversary.
Therefore the ability to use cognitive prosthetics to study existing or planned systems will show itself to be a high value pursuit going forward.
Additionally by way of extension we posit that whereas the table below suggests a larger number of CI's that are able to communicate we would also take the position that any of these specific CI's might themselves be capable of communicating with an ensemble of comparable size independently of of how it was communicating with this top layer ensemble.
| P 1 | P 2 | P 3 | P 4 | P 5 | P 6 | P 7 | P 8 |
|---|---|---|---|---|---|---|---|
| CG4.10 | CG4.11 | IBM.12 | IBM.13 | CG4.10 | CG4.11 | IBM.12 | IBM.13 |
| CG4.20 | CG4.21 | IBM.22 | IBM.23 | CG4.10 | CG4.11 | IBM.12 | IBM.13|- |
| CG4.40 | * | * | * | IBM.01 | CG4.01 | * | * |
| IBM.01 | CG4.01 | * | * | IBM.01 | CG4.01 | * | * |
| CG4.10 | CG4.11 | IBM.12 | IBM.13 | CG4.10 | CG4.11 | IBM.12 | IBM.13 |
| CG4.20 | CG4.21 | IBM.22 | IBM.23 | CG4.10 | CG4.11 | IBM.12 | IBM.13|- |
| CG4.40 | * | * | * | IBM.01 | CG4.01 | * | * |
| IBM.01 | CG4.01 | * | * | IBM.01 | CG4.01 | * | * |
Note the CE configuration in the above table. We posit that collections of cognitive appliances can be gathered together into considerably larger numbers. The increased numbers would increase the granularity and therefore the precision of a proposed model. The actual level of resolution would be driven by the requirements of the organization that held the responsibility to deliver reliable, credible results.
Boundaries Exploration. These might emerge as compelling social, economic, political policy proposals grounded in common sense; possible ways to solve older, existing problems using recent insights into the mechanics, linkages and dynamics of observable processes;
New Value Propositions. Near term job market realignment, disruption; (increased social dislocation, disruption). According to the British financial management firm XYZ.PQR source data set information can be provided to CG4 by converting the desired textual material as a .txt file and entering it directly. It can then be preprocessed such that structuring and prompt elements are provided for the system to use to return responses.
Looking forward we can foresee the prospect that a new support sector might emerge that provides rapid knowledge capture and preprocessing services. It would make use of high speed text and image capture. Optical character reading (OCR) capabilities would then render the captured images into processable text.
Isakara Labs in Tokyo demonstrates how their research can capture 250 book pages of text per minute. One can imagine a small enterprise with a teams of individuals whose tasks would include book capture then conversion to variously text or PDF format for loading into the training data for specific purposes.
Locus of Interest: Emergence of position nexus ecology; crystallization of political polarization; these might be further developments of existing “channels” currently available on youtube.com; but would operate independently of that platform, but become accessible via a “white pages” type structure;
Food Chain: The emergence of specialist groups dedicated to supporting various actors in the nexus ecology; these will follow existing business development lines with market segmentation and brand identification; we should expect to see emerging markets with offerings that are priced as: high, best, low and niche;
Because of the novelty of these new technologies we should also expect to see the emergence of a set of market places that reflect those found in most commercial settings; this means that there will be;
Market Positions by Price - High, Niche, Best, Low:
We should expect to see a rapidly developing market place for new value propositions. These will involve the exchange for ideas, capabilities and services. This marketplace will probably evolve rapidly and shadow the development of the software market place. Initially when there were very few software vendors and the marketplace was perceived to be small then prices for individual software items was substantial. A spreadsheet tool such as Lotus 1-2-3 ran in the hundreds of US dollars. As the marketplace grew prices came down. As perceptions of the size of the marketplace sharpened new products and service providers appeared and the prices gradually fell. We should expect to see a comparable shakeout in the emerging market place of cognitive "fittings", "couplers" and other forms of connectivity.
Open markets (Official Market) These will be openly and easily accessible and provide buyers and sellers a readily accessible location to enact their exchanges.
What may develop will be a marketplace like any other open, above board marketplace of buyers and sellers. These can be found scattered all over any given major web paged. They often involve being obliged to see and respond to a pop up add in order to view the desired content.
What will also shadow this open marketplace will be gray and black market places wherein items are available for exchange that have not yet received full sanction of the host society.
Recognized Unofficial Markets (gray market). These can be expected to be venues in which are in unregulated venues; they might be located geographically anywhere on the planet;
Covert Markets (black market). we should expect that these venues will function as they always have; unregulated and very much caveat emptor;
Some Talking Points. Following are a few talking point topics that might serve as a point of entre into the discussion of what kinds of risks CG4 and its variants might pose. We recognize that risks might manifest from malicious actors, systemically and organically or, by way of speculation, using our insight and knowledge about how earlier technologies required regulation and management. We recognize that control of these new technologies may be required insofar as the benefit that they offer might outweigh the downsides of their use. As in prior technologies there may be the need to demand licensing, registration or other forms of regulation. In the meantime we recognize the reality that human nature has shown itself to be immutable across the span of written history. Therefore we should expect that even if some form of regulation or licensing emerges with this technology there will always be so-called "black markets". The talking points that follow defer discussions of moral imperatives but instead focus upon the possible, knowing what we know about the realities of human behavior. They therefore serve only as a means to spotlight the more obvious uses that this emerging technology might come to light.
Problem Characteristics. (these need a) a sanity-check b) another consistency pass, find the center of gravity and redistribute focus accordingly);
Perceptions. {Provocations False-Flag Misdirection Compromise }
Beliefs. The major western societies have belatedly discovered that managing perceptions and beliefs has become a major problem. The arrival of broadly accessible social media have created communications environments that can serve up the full range of audio and video content.
And this can all be done with or without any prior vetting, verification or editing; recent developments with tools such as CG4, Dall-E, and MidJourney have enabled the creation of remarkably convincing reports, documentaries and images; which in all cases can be made almost indistinguishable from reality; this trend will continue to refine to the point that it will require very special and powerful tools to decipher fact from fiction; the more sophisticated creation tools will simply lengthen the time required to correct public perceptions and beliefs about what is or is not true.
This will prove to have created an environment in which risks to societies in terms of disruption, dissention and violence will be escalated;
These tools will presently arrive at a state wherein a small group of dedicated and competent individuals will be able to create content that will rival any evening news report; which can set in motion social movements that the responsible civil authorities will find challenging to diffuse. This situation has already become the new norm. This can easily be recognized by reviewing how current events political narratives are presented; it is no longer surprising to encounter dozens of "news" reports with the most remarkably inflammatory tag lines or claims; going forward the sophistication that political and social messaging will reach the point that whole new communities will crystallize; currently much of the fare that is viewable caters to communities of interest; going forward elements of these communities will coalesce into communities of action - with the result that actual "facts on the ground" will shift in possibly sudden and unexpected ways;
Extortion. The Office of Personnel Management breach in 2014 signaled the fact that a broad swathe of individuals who operate in extremely sensitive roles can be placed at risk overnight; the severity of this breach can not be overstated because of the fact that in almost all cases the individual who have been identified have had their personal identifying features revealed for the whole planet to peruse; a hostile actor can now collect all of this information, analyze it and create mapping information that reveal associations, travel patterns, chain of command and any number of other revealing insights; any and all of these can then be used as leverage against any of these individuals;
Nano-Scale Fabrication. The ability to fabricate extremely novel pharmaceuticals is palpable. Given that there are tools available for the creation of molecular structures with remarkable and novel features, traits and characteristics means that the range of possible uses can not be foreseen. The inherent risks associated with the creation of heretofore unheard of or even unimagined materials and drugs can not be underestimated. We should expect to see materials with strengths that rival or exceed those found in nature, a prime example is spider's silk; which is known to be multiple times stronger than steel and far less brittle;
The availability of polymeric molecules such as dendrimers means that a facility with the requisite tools and skills will be able to turn out on-demand ethical drugs that can only be guessed at; were an actor or agency wish, pharmaceutical substances can be fabricated wherein their effects can be modulated - to successively be more or less intense for durations that only the designer can specify; this means that powerful mood and perception altering psycho-actives can be fabricated and delivered using means that are untraceable and extremely surreptitious;
By way of example, one can envision a dendrimer molecule, possibly a set of these being released into a religious gathering; by way of illustration, suppose that a powerful psychological disinhibiter were to be embedded within a low generation (six layers for instance) multiple layers could contain concentrations of this disinhibiter; each layer could be designed to have a solubility quotient whereby it might dissolve either more quickly or more slowly.
Individuals subjected to airborne dosages of this psychoactive could find themselves experiencing waves of mental relaxation; any suggestive external stimuli might add to the effect such that verbal suggestions, or possibly visual imagery could be sufficient to induce behavior in corresponding to that stimuli. Current neuro-anatomy mapping suggests that this technology can be tailored to act upon highly specific cortical regions; add in the possibility of delayed release of successive psycho-actives and we can be faced with situations wherein substantial numbers of individual can be induced into unexpected and even possibly uncontrollable personal behaviors.
In order to make a preliminary assessment as to whether and how the original questions posed at the beginning of this exercise can be answered we summarize them in the following. From there we attempt to suggest possible answers.
However this would seem to mean that a synopsis of the various types of risks described above might need to be used as a baseline against which to assess the questions as they have been posed. To that end we attempt to summarize the more glaring instances of risks that seem to entail considerable and immediate risk to the "here and now" world that we all inhabit. Suppose that we postulate the above to be so, we do believe that risks described as theoretical or systemic could come into existence sooner than most observers expect. Therefore we will use this as a staring point.
Risks. {Systemic Malicious Theoretical (SMT)}.
To list a few that seem to be most imminent and pressing:
- Manufactured or Manipulated Realities and Narratives.
- The ability to craft ultra-realistic messages involving texts, ultra lifelike avatars that make claims about individuals, events or conditions that are not true.
- Sentiment manipulation such as that created by Cambridge Analytica.
- The ability to use and control existing infrastructure (communications, power, civil systems) to cause unplanned outages, wreak chaos, panic and confusion.
- The intrinsic pressures involved in an industrial process to adapt the most recent tools and techniques to maintain competitive standing.
- Intrinsic Obsolescence.
- We can see this in strike activities such as the (WGA strike of screen writers) or in other venues.
- Marginalization of transportation workers through self driving vehicles (automobiles, trucks, busses).
- Thinning of professional ranks such as software developers, legal, medical professionals.
- Marginalization of educational professionals.
- Narrowing and steepening of of academic oriented ladders.
- Boosted scientific advances.
- AI designed chemistry, biology, other scientific experiments toward the end of creating new materials, pharmaceuticals and other substances and materials.
- Rapid to instant dissemination of research and design information focusing on advanced dual use tools, materials and substances.
- Accelerated domain knowledge refinement and modeling.
- Modeling tools that allow for highly realistic and exquisitely detailed analysis of economic, social, political and geopolitical systems.
- Emergence of new market places offering heretofore unavailable pharmaceuticals, processing tools or other forms of control.